All The Talks 2020 - Security
Talks
Catching Cybercriminals Pandering to the Pandemic
Since the initial outbreak of COVID-19, cybercriminals have since found many ways to take advantage of anxious and fearful users. There have been reports of TrickBot campaigns, Ryuk ransomware targeting hospitals, and hackers hijacking routers’ DN...
Tarik Saleh, Chad Anderson
Security
Dumpster Fires: 3 things about IR I learned by being a firefighter
Threats surround us like a ring of burning fire. Unfortunately, incident response doesn't come naturally to an operational mindset where the focus tends to be on reactive problem solving. As a volunteer firefighter for over twenty years, the prese...
Catherine J Ullman
Security
Hacker Rights
Sixty percent of hackers don’t submit vulnerabilities due to the fear of out-of-date legislation, press coverage, and companies misdirected policies. This talk will focus on increasing public awareness in order to bring legislation that supports e...
Chloe Messdaghi
Security
Web Components for Authentication: The what, the how and the why
In this talk, we will take a look at what Web Components are, what they consist of and how to build them. Then we will see what advantages Web Components have when approaching and implementing authentication into our application, how Web Component...
Ana Cidre
Security
Securing eHealth and eGovernment with Java
The EU increases its cooperation on cyber defence to strengthen its resilience to cyber-attacks through the EU Cybersecurity Act and certification of products, services or applications. To be as well prepared as possible against hacker attacks or ...
Thodoris Bais
Java
Security
Get testing bottlenecks out of your deployment pipeline
In the modern day SDDC, the ability to create a VM or template consistent, repeatable, and streamlined is a requirement. Using open source projects like Packer, Ansible, and InSpec you can build this nirvana. Using Packer to create a template, Ans...
JJ Asghar
Security
Stealing Reality – Exploiting the Human Element with Deep Fakes
As a result of explosive advancements in the capabilities of neural networks, deep fake media has become increasingly convincing and easy to produce. Experts have warned of the impact this could have on elections and personal security. Additionall...
Alyssa Miller
Security
The Three Things All Web Professionals Need To Know About Privacy
Clients trust web professionals to guide them to a website that generates leads. An unfortunate side effect of lead generation is the collection of personal information. For example, a website that has a contact form that collects a name and an em...
Donata Kalnenaite
Security
The Pentester Blueprint: A Guide to Becoming a Pentester
Pentesting or ethical hacking as it is more commonly known has become a much sought-after job by people in IT, InfoSec, or those just trying to get into the industry. In this presentation, Phillip Wylie shares the blueprint for becoming a penteste...
Phillip Wylie
Hacking
Security
Why Developers Struggle with AppSec
We’ve all heard the buzz around pushing application security into the hands of developers, but if you’re like most companies, it has been hard to actually make this a reality. You aren’t alone - putting the culture, processes, and tooling into pla...
Scott Gerlach
Security
Trust me, we're doing devsecops
Many of the Dev*Ops talks revolve around tools and culture. There are some good, fascinating talks all shouting: “All for the great (business) good!” Yet, they rarely address topics at the interpersonal, relationship level. Pipelines and automatio...
Patrick Debois
Security
Observability for Security and Audit
When organizations are moving to the cloud, security is usually seen as an obstacle. Often the focus is on replicating the controls they have in their existing environments. However shifting to a different mindset, the cloud actually enables new l...
Mike Milner
Security
Unlimited WiFi: Bypass Captive Portals and Proxies with a Twist!
Have you ever been stuck in the airport and run out of the one hour free WiFi? Have you ever been in a hotel that makes you pay for WiFi? Our talk, Unlimited WiFi, helps understand the common flaws within captive portals and proxies. On restricted...
Sajeeb Lohani
Security
Applying Fraud Detection Techniques to Hunt Adversaries
Like information security professionals, fraud analysts are inundated with data and often experience alert fatigue. As a former fraud analyst, I was often wasting time chasing false positives and I felt as though I wasn’t making a difference. By i...
Nicole Hoffman
Security
Continuous Hacking
There are so many sophisticated ways to exploit web applications, that it’s almost impossible for a developer to write completely secure code. But we can’t accept this situation. We can’t expose our users (and our user's data) to hackers. So wh...
Omer Levi Hevroni
Security
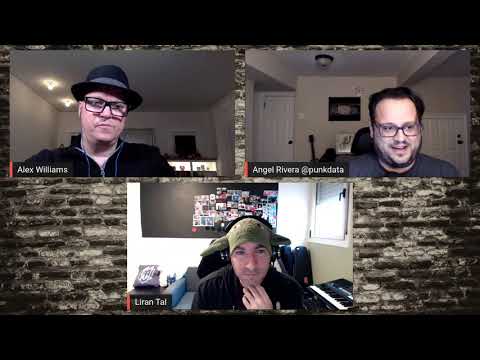
Using Security as a Catalyst for Faster Development With DevSecOps
While almost half of developers and operations teams say security slows them down, some organizations are actually using security as a catalyst to adopt application architectures that allow them to move fast but also securely. These teams are inte...
Angel, Alex, Liran.
Security
Migrating existing IAM to least-privilege IAM as IaC
Public cloud providers are now offering more mature and better integrated IAM services. The AWS IAM service is natively integrated with every AWS service and makes it simple to set up, connect and integrate services using various access control me...
Nimrod Kor
Security
How to put the "Sec" in "DevSecOps" (and make sure it actually works)
In the ancient times of software creation, we had AppSec, and we had developers. Generally, AppSec was aware of security problems, their impact, and code-level fixes. However, these remedies would rarely work in the custom tech stack of the co...
Matias Madou
Security
Basics of OAuth 2.0 and OpenID Connect
Microservice architectures bring many benefits to software applications. But at the same time, new challenges of distributed systems have also been introduced. One of these challenges is how to implement a flexible, secure and efficient authentica...
Andreas Falk
OAuth
OopenID Connect
Security
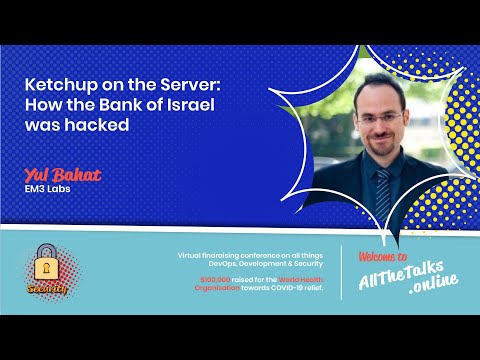
Ketchup on the Server: How the Bank of Israel was hacked
In 2008, the official website of the central Bank of Israel was defaced to include anti-Israeli propaganda. The forensic investigation that followed revealed massive oversights, misconfigurations, security holes and a general complete lack of awar...
Yul Bahat
Security
How to Hack OAuth
OAuth is the foundation of most of modern online security, used everywhere from signing in to mobile apps, to protecting your bank accounts. Despite its ubiquity, it is still often difficult to implement safely and securely, especially in today's ...
Aaron Parecki
Hacking
Security
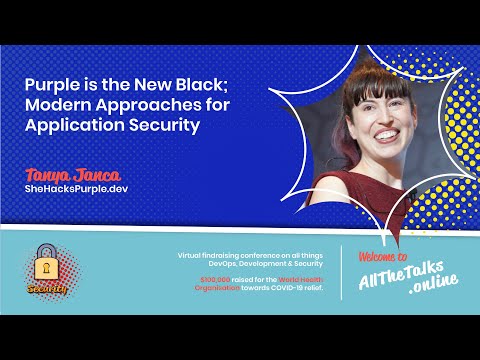
Purple is the New Black; Modern Approaches for Application Security
Gone are the days when breaches were rare and security could safely be put low on the priority list; product security is now a customer demand and cyber crime has reached epic proportions. Our idolization of hackers, penetration testing and ‘break...
Tanya Janca
Security