DevSecCon24 2020
Talks
Securing the Pipeline with Open Source Tools
This talk digs into the fundamentals of DevSecOps, exploring the key principles required to advance your security practices. Considering the changes in culture, methodologies, and tools, it will demonstrate how to accelerate your team journey’s fr...
Michelle Ribeiro
Security
Infrastructure-as-code Security: Why, What, and How
Planning, provisioning, and changing infrastructure are becoming vital to rapid cloud application development. Incorporating infrastructure-as-code into software development promotes transparency and helps prevent bad configurations upstream, but ...
Barak Schoster
Security
Securing Containers by Breaking in
There’s no better way to understand container security than seeing some live hacking! This session introduces the state of docker security by reviewing vulnerabilities in docker images and their impact on applications, and demonstrates via hands-o...
Simon Maple
Security
A Crash Course in Audit Logs
Application audit logs include a breadcrumb trail of all user activity and the logs are used to answer many different questions in a variety of contexts. Development teams perform analytics on the logs. Security teams write threat detection logic ...
Justin Massey
The Hacker Hippocampus
Always on the edge of your seat when it comes to new exploits and tricks. From bug bounties, CTFs, live hacking events, simulations, and interactive educational modules, they have been proven to stimulate and enforce new tools and knowledge to bec...
Chloe Messdaghi
Security
How to Verify for Security Early and Often
In many organizations testing for security is done following a “scan-then-fix” approach. The security team runs a scanning tool or conducts a pen test, triages the results, and then presents the development team a long list of vulnerabilities to...
Katy Anton
Security
Fireside Chat: Reality Check on Deep Fakes
Join security advocate Alyssa Miller, journalist J.M. Porup, and privacy & patients rights advocate Andrea Downing for this open conversation about Deepfakes. They'll talk about the technology behind deepfakes including some of the most research d...
Alyssa Miller, J.M. Porup, Andrea Downing
The Evolution of the Software Supply Chain Attack
Malicious hackers are becoming increasingly adept at attacking the underbelly of the Software Supply Chain. To cause the most damage whilst remaining undetected, hackers are rapidly evolving their attack methods. For the past four years, the St...
Ilkka Turunen
The biggest security talent pool you’ve never heard of
At a time of huge shortages in technology talent projected to reach 3 million globally by 2022, businesses are in search of creative solutions. On the other hand, autistic people face huge employment barriers despite many having highly sought afte...
Mike Tozer
Security
Collection is not detection and other rules for modernising sec ops
Security operations has always been hard. How many logs should we collect? Which logs should we collect? How to we respond and remediate things quickly? Then just when you thought you'd got it right for your on-premises, you've decided to move the...
Sarah Young
Security
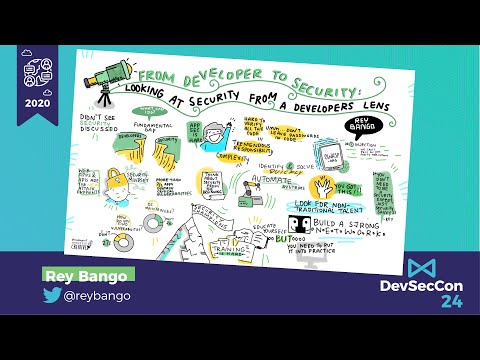
From Developer to Security: Looking at Security from a Developer Lens
I've spent roughly 18 years building sites and apps for the web and while I always did my best to apply the basics of security, I never truly understood the many ways systems could be hacked. So I decided to do something about it. A year into my ...
Rey Bango
Security
Benefits of Continuous Security & Compliance for Cloud Infrastructure
Learn how Cloud Architects and DevSecOps teams can bring continuous security awareness, visibility and fixes to their cloud infrastructure and services for governance and operational excellence, helping to reduce cloud misconfigurations and secu...
Fernando Cardoso
Security
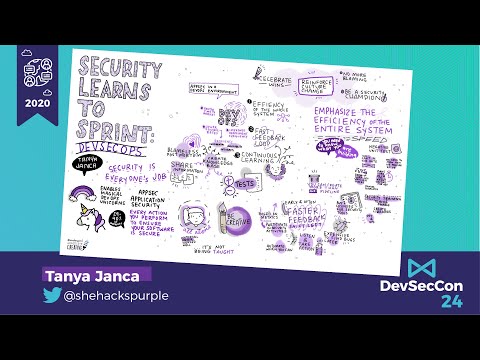
Security Learns to Sprint: DevSecOps
This talk will argue that DevOps could be the best thing to happen to application security since OWASP, if developers and operations teams are enabled to make security a part of their everyday work. With a ratio of 100/10/1 for Development, Operat...
Tanya Janca
Security
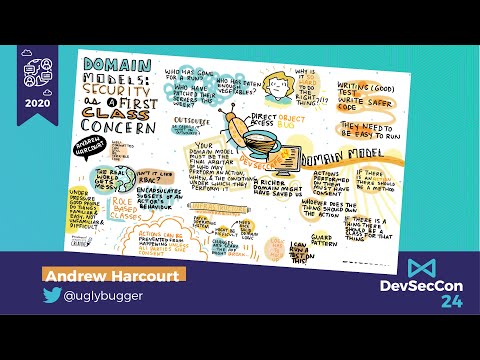
Domain models: security as a first-class concern
Integrating security into the development process is critical for the proper functioning of an application. API gateways, RBAC systems, service mesh sidecars etc. can all provide some elements of security but the final arbiter of who can do what a...
Andrew Harcourt
Security
Hardening your soft software supply chain
Software supply chain threats are real! As more developers and companies rely on open-source code - that anyone can contribute to, including attackers - this opens the door to a new vector of attack. There are increasing supply chain compromises w...
Maya Kaczorowski
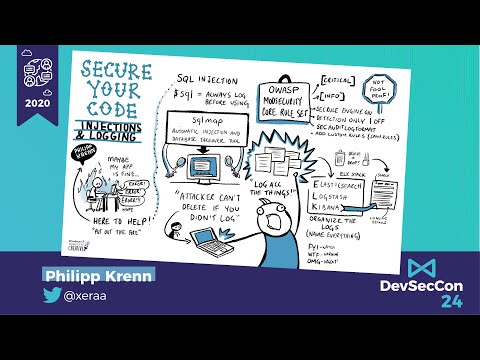
Secure Your Code — Injections and Logging
Security is a hard problem, especially when you are only running but not writing an application. The infamous comic "This is fine" is often the best description we have for this scenario. But it doesn’t have to be. This talks shows how to protect ...
Philipp Krenn
Security
Modern Dynamic Application Security Testing
Dynamic Application Security Testing has developed a bad rap. Application Security as a whole has struggled to keep up with the shifts in modern software delivery, and that is especially true for dynamic application scanning. However, the ability ...
Scott Gerlach
Security
Going DevOps: Why „top down or bottom up” might be the wrong question!
Sabine Wojcieszak
DevOps
Security
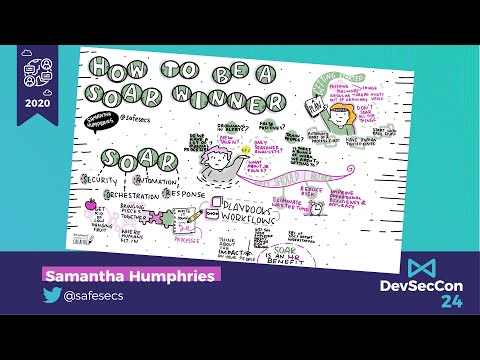
How to be a SOAR winner
Security orchestration, automation, and response (a.k.a. SOAR) is the cool kid on the block in security right now. Implementing SOAR requires a both a strategic and a tactical approach, in order to avoid pitfalls and ensure ongoing success. Consid...
Samantha Humphries
Security
Building an Observable Infrastructure and Code
With microservices every outage is like a murder mystery” is a common complaint. But it doesn’t have to be! With the evolution of the open source tools and technologies, we can monitor our service level availability, logs, security events and Appl...
Aravind Putrevu
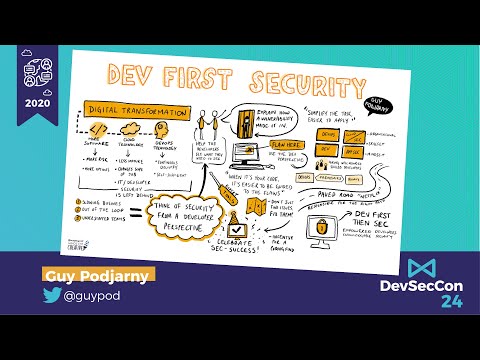
Dev-First Security: Learning from the pioneers
Digital Transformation, and notably Cloud and DevOps, have radically changed how we run our business and build software, and yet security practices in most companies remain largely unchanged, and so are left behind. This talk shares practices and...
Guy Podjarny
Security
AppSec is dead. Long live DevSecOps!
In the ancient times of software creation, we had AppSec, and we had developers. Generally, AppSec was aware of security problems, their impact, and code-level fixes. However, these remedies would rarely work in the custom tech stack of the com...
Matias Madou
Security
The Joys Of Integrating Security Testing Into Your Pipeline
(Moderated) Michael Man Panelists: Dr. Wendy Ng Liz Rice Grant Douglas Ashraf Aboukass Katie Gamanji
Katie Gamanji, Dr. Wendy Ng, Liz Rice, Grant Douglas, Ashraf Aboukass
Security
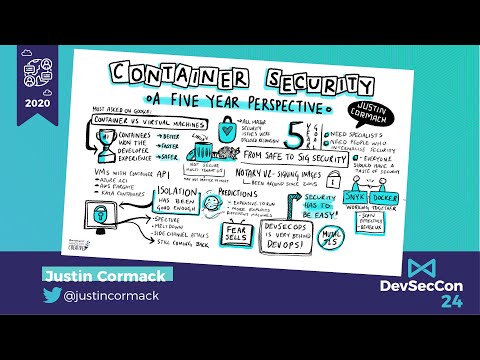
Container Security: A Five Year Perspective
I have been working for five years in container security. A long time in a fast moving field, and much has changed in the container ecosystem. And also, much has stayed the same. This talk is about the successes and failures and the ones that got ...
Justin Cormack
Security
When Stress Meets Tech
No matter what profession you are in, our jobs can contain a variety of stress factors, which are unknown to individuals looking from the outside. This is a lecture-based on research that recommends corporations should devote to IT-specific emplo...
Crux Conception
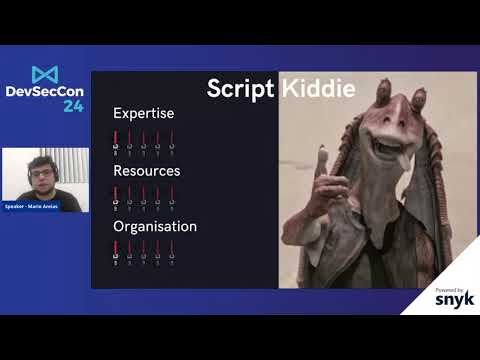
Threat Modeling the Death Star
It is a known fact the Empire needs to up their security game. The Rebellion hack their ships, steal their plans and even create backdoors! In this talk we will help the Empire by threat modelling the Death Star. Traditionally, Threat Models ha...
Mário Areias
Security
Lessons Learned from the DevSecOps Trenches
This panel is made up of practitioners who lead application security teams at the forefront of the DevSecOps shift at companies such as Dropbox, Netflix, Datadog, and Signal Sciences. We will share a number of lessons we had to learn the hard way ...
Tanya Janca, Doug DePerry, Zane Lackey, Justine Osborne, Clint Gibler