BSidesSLC 2020
Talks
BOLA, IDOR, MA, BFLA. Welcome to the OWASP API Top 10!
A foundational element of innovation in today’s app-driven world is the API. APIs are a critical part of modern mobile, SaaS and web applications and can be found in customer-facing, partner-facing and internal applications. By nature, APIs expos...
Adam Fisher
Security
From Mattress sales to Infosec soldier
This session will cover my story of transitioning from a Mattress Salesman to a Security Analyst. Anyone can make it in this industry if you have the drive and passion. Attend if you're still deciding on which path in infosec to take.
Chriss Hansen
Security
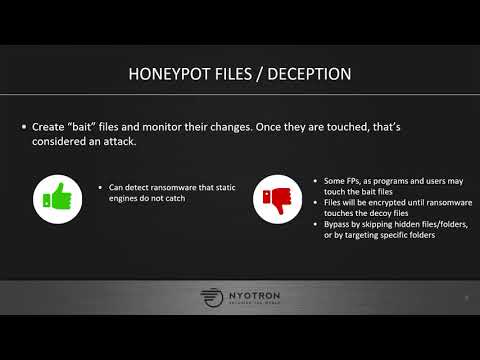
Rendering Ransomware Detection and EDR Products Blind
This talk will cover a Windows evasion technique called “RIPlace” that, when used to maliciously alter files, bypasses most existing ransomware protection technologiesI will review existing ransomware detection methods, the workflow of a typical r...
Rene Kolga
Security
Where's my dough?! A look at web skimming attacks on
The session is about an emerging threat called web-skimming that has been used to compromise millions of credit cards. Attendees will learn about innovative techniques hackers have used to steal credit cards from e-commerce websites and what devel...
Siddharth Coontoor
Security
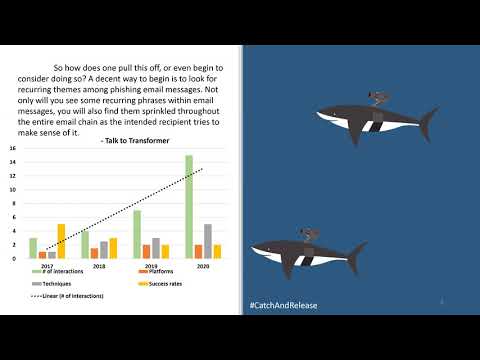
It Is The Year 200, We Are Robots
OpenAI talked about the theoretical abuse cases for large language models - we will prove their fears to be legitimate. In this talk we'll explore the use of language models to generate synthetic phishing emails, and build chat-bots to add a perso...
Will Pearce
Security
The Domain Password Audit Tool
Poor password habits often lead to system compromise. The Roberts family has authored an open source tool called “The Domain Password Audit Tool (DPAT)” and will be presenting how it can be used to understand weak password use. The discussion wil...
Cameron Roberts, Darin Roberts, Carrie Roberts
Security
A Chain Is No Stronger Than Its Weakest LNK
Attackers continue to abuse Windows shortcut (LNK) files to gain initial access to their targeted networks, maintain persistence, and execute malicious scripts. This presentation will familiarize practitioners with the ways in which adversaries ab...
David French
Security
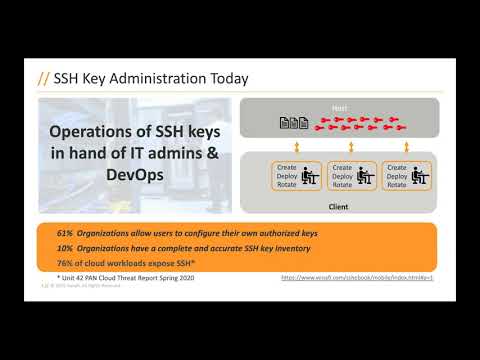
SSH Keys: Security Asset or Liability?
SSH keys are widely used in every enterprise to provide privileged administrative access. Poor SSH key management practices expose businesses to costly security risks. Learn how to take SSH keys from an operational liability to a security asset.
Bart Lenaerts
Security
Cloud-Based Contextual Analysis as Code
Explore the power behind software defined contextual analysis in the cloud that allows DevOps and Security teams to be more proactive without disrupting their day to day operations.
Erkang Zheng
Security
How Can I Get Started in Cybersecurity?
Aimed at new, or less experienced cyber professionals, this presentation will review a wealth of online resources to help get you started in your area of interest. Penetration testing, reverse engineering, compliance, forensics and incident respon...
Dale Rowe
Security
$how Me the Money! (Getting Business Buy-in)
Having trouble getting execs to buy into the idea of security? This talk is a crash course in getting business buy-in to securing your organization, and getting user buy-in, too. I'll share some spreadsheet tools that will help the business unders...
Carlota Sage
Security
MineMeld - there's gold in them thar hills!
MineMeld is an open source, extensible Threat Intelligence processing framework. In this session you'll learn how to install MineMeld and set up common configurations. We'll also cover adding new and custom sources and how to integrate outputs in...
Jason Reverri
Security