Black Hat Europe 2019
Talks
Practical Side-Channel Attacks Against WPA-TKIP
Wireless networks and their security protocols keep evolving due to increased performance and reliability demands. For instance, recently the Wi-Fi Alliance released WPA3, which offers better security guarantees (e.g., longer keys). In light of th...
Domien Schepers, Mathy Vanhoef
Security
Fuzzing and Exploiting Virtual Channels in Microsoft Remote Desktop Protocol for Fun and Profit
In this talk, we share our adventure in applying coverage-based fuzzing to the RDP client, more specifically, virtual channels in RDP. In the RDP client, virtual channels deal with complex functionalities of RDP such as Sound, Graphics (GDI and Re...
Ki Taek Lee, Yeongjin Jang, Chun Sung Park, Seungjoo Kim
Security
Security Holes in the Integration and Management of Messaging Protocols on Commercial IoT Clouds
In this presentation, we report the first systematic study on the protection that leading commercial IoT clouds (e.g., AWS IoT Core, IBM Watson IoT, Azure IoT, Google Cloud IoT, Alibaba IoT, Tuya Smart) put in place for integrating MQTT to device-...
Yuqing Zhang, Yan Jia, Luyi Xing
Security
Decisions and Revisions - The Ever Evolving Face of the Black Hat NOC
This session is your chance to get up close and personal with the Black Hat NOC. We'll walk you through the process of deciding what equipment and services we deploy on the Black Hat network, and our reasoning around those decisions. We'll also di...
Neil Wyler, Bart Stump
Security
Locknote: Conclusions and Key Takeaways from Black Hat Europe 2019
At the close of this year's conference, join Black Hat Founder Jeff Moss and members of the esteemed Black Hat Review Board for an insightful conversation on the most pressing issues facing the InfoSec community. This Locknote will feature a candi...
Jeff Moss, Leigh-Anne Galloway, Marina Krotofil, Daniel Cuthbert
Security
Far Sides of Java Remote Protocols
Java Remote Method Invocation (RMI) and Common Object Request Broker Architecture (CORBA) are widely deployed mechanisms for cross-process communications. In this talk, we will walk through the technical workflow of the technologies, revealing sev...
An Trinh
Java
Security
Hackers, Journalists and the Ethical Swamp
In this talk, investigative journalist Geoff White (who has covered technology for, among others, BBC News, Channel 4 News and Forbes) takes five high-profile hacking incidents and analyses how they reflect key trends and tactics for working with ...
Geoff White
Security
OEM Finder: Hunting Vulnerable OEM IoT Devices at Scale
Using this tool, we found more than 180 unique vulnerable OEM device candidates from over 50,000 IoT device images, which we had collected from EC websites. Furthermore, we analyzed the latest firmware image of some of these OEM device candidates,...
Asuka Nakajima
Security
What the Fuzz
Come to our talk and find out, what state-of-the-art fuzzing technologies have to offer, and what is yet to come. This talk will feature demos, CVEs, and a release, as well as lots of stuff we learned over the last four years of fuzzing research. ...
Sergej Schumilo, Cornelius Aschermann
Security
Keynote: Blue to Red: Traversing the Spectrum
The rising demand for talent to fill thousands of open roles in the security industry has resulted in one significant consequence: overspecialization. This can hinder someone from thinking about the larger picture of security challenges they face ...
Amanda Rousseau
Security
BluePill: Neutralizing Anti-Analysis Behavior in Malware Dissection
Designed around analysts, BluePill lets them customize its hooks and add new ones using insight from the dissection, which is especially useful for targeted malware and new tricks. Also, it is immune from semantic gaps. In this talk, I will show h...
Daniele Cono D'Elia
Security
Bypassing KPTI Using the Speculative Behavior of the SWAPGS Instruction
Speculative-execution based attacks and side-channels are more and more common as disclosures continue to increase scrutiny by researchers in this field. In this talk, we demonstrate a new type of side-channel attack based on speculative execution...
Dan Lutas, Andrei Lutas
Security
BlueMaster: Bypassing and Fixing Bluetooth-based Proximity Authentication
In this talk, we present the security pitfalls of Bluetooth-based proximity authentication. We analyzed implementations of Android Smart Lock and Windows Dynamic Lock and demonstrated new attacks on these implementations. Based on our analysis, we...
Yeongjin Jang, Junbum Shin, Youngman Jung
Security
Conducting a Successful False Flag Cyber Operation (Blame it on China)
Cyber attribution is hard, really hard. But luckily for attackers, a new armchair analyst is born every minute. Given any high profile hack, Captain Attribution™ is sure to show up and tell you how obvious it is that {China|Russia|USA|Israel|Iran|...
Jake Williams
Security
Tackling Privilege Escalation with Offense and Defense
We will describe some of the surprising discoveries by researchers submitting to the Zero Day Initiative program, which were used to verify the application hardening as it occurred. Over the years, this multi-pronged approach eliminated a large se...
Abdul-Aziz Hariri, Edgar Pek
Security
Unveiling the Underground World of Anti-Cheats
This talk pretends to catch everyone's attention from new people to experts on the field, starting with a state of the market and interesting cases around the cheating world, and finishing with a deep explanation of each analyzed technique and the...
Joel Noguera
Security
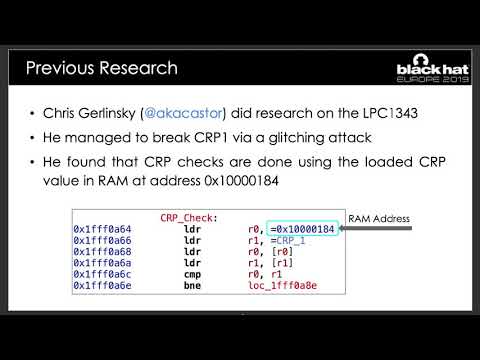
Breaking Bootloaders on the Cheap
For this presentation, we reverse-engineered and analysed the bootloaders of three widely used microcontrollers (NXP LPC1343, ST STM32F4, and ST STM8) in order to assess if the readout protection can be overcome with software-based attacks. Our...
David Oswald, Qais Temeiza
Security
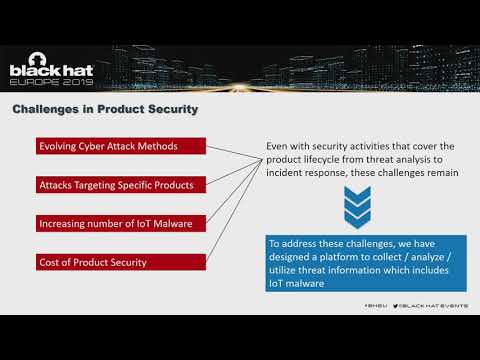
Understanding the IoT Threat Landscape
In this session, we will discuss the details of this project and share some analysis of malware that have been collected. By leveraging this information, Panasonic aims to develop products that are resilient to malware. In addition, we are looking...
Hikohiro Y Lin, Yuki Osawa
Security
Hands Off and Putting SLAB/SLUB Feng Shui in a Blackbox
In this talk, we will introduce a precise automated memory layout manipulation technique. We will demonstrate that using this manipulation technique, an attacker could not only easily identify the system calls tied to the objects of interest but, ...
Xinyu Xing, Yueqi Chen, Jimmy Su
Security
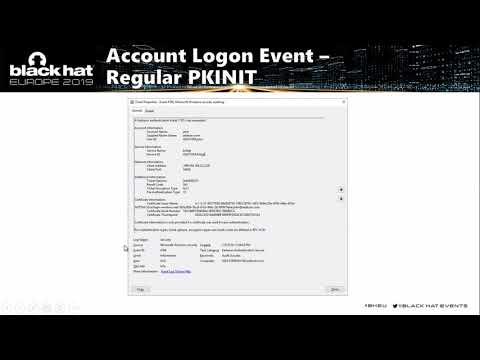
Exploiting Windows Hello for Business
During this talk, we will also demonstrate our new toolset that can be used to scan corporate environments for the aforementioned vulnerabilities and to resolve any issues found. It also provides a much-required visibility into Windows Hello for B...
Michael Grafnetter
Security
Inside Out - The Cloud has Never been so Close
In this talk, we present an alternative new approach for attacking cloud infrastructure. We use graphs to build and illustrate the relationships between different resources, identities, and policies. After mapping all the relationships, we show ho...
Igal Gofman, Yaron Shani
Security
How to Break PDF Encryption
PDF is among the most widely used document formats worldwide. To ensure confidentiality, PDF supports document encryption. In this talk, we analyze PDF encryption and show two novel techniques for breaking the confidentiality of encrypted document...
Jens Müller, Fabian Ising
Security
Bring Your Own Token to Replace the Traditional Smartcards for Strong Authentication and Signing
This whitepaper describes the solution implemented at Cisco, to replace the traditional hybrid smartcards with Bring Your Own Token (BYOT) model, to overcome the limitations and challenges with the traditional smartcard solutions. The solution ena...
Karthik Ramasamy, Eric Hampshire
Security
ClusterFuzz: Fuzzing at Google Scale
This talk is about how we overcame these challenges to operate the largest publicly known fuzzing infrastructure, running over 25,000 cores, 2,500 targets and find over 8,000 security vulnerabilities in several Google products and 200 open source ...
Oliver Chang, Abhishek Arya
Security
Advanced VBA Macros Attack & Defence
In 2019, VBA macros are still heavily used to deliver malware, and new obfuscation techniques such as VBA Stomping implemented in EvilClippy allow attackers to deliver malicious payloads to end users without being detected. Luckily, analysis and d...
Philippe Lagadec
Security
Is Your Mental Health for Sale?
In this talk, we will highlight what type of third parties can be found on mental health-related websites, how frequently some trackers can be found, and what type of tracking they enable. We will then take you on a journey to see exactly what dat...
Eliot Bendinelli, Frederike Kaltheuner
Security
Booting the iOS Kernel to an Interactive Bash Shell on QEMU
Booting the iOS kernel on QEMU with an interactive bash shell and a live debugger attached to the kernel. A major step forward in the direction of having a full iOS open source system emulator on QEMU. The research details and demo will be present...
Jonathan Afek
Security
iOS
Alexa, Hack My Server(less) Please
When adopting serverless technology, we eliminate the need to manage a server for our application. By doing so, we also pass some of the security threats to the cloud provider. We do not need to care about OS patching and configuration any more. I...
Tal Melamed
Security
Serverless
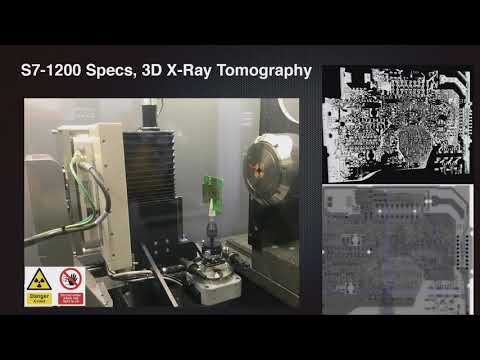
Doors of Durin: The Veiled Gate to Siemens S7 Silicon
Siemens is a leading provider of industrial automation components for critical infrastructures, and their S7 PLC series is one of the most widely used PLCs in the industry. In recent years, Siemens integrated various security measures into their P...
Thorsten Holz, Ali Abbasi, Tobias Scharnowski
Security
Unleashing the Power of My 20+ Years Old Car
In this talk, I will give a brief introduction on how I managed to bypass that limiter, how I could have done it, how I ended up doing it, and what I discovered along the way. Automotive engine computer management will be introduced, as well as...
Stanislas Lejay
Security
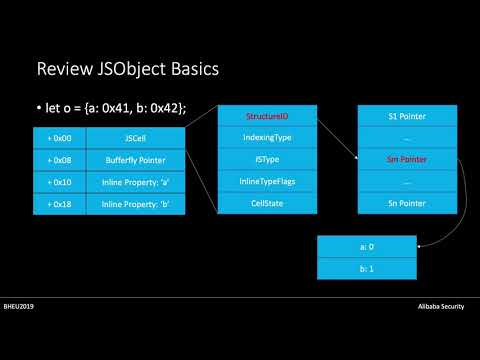
Thinking Outside the JIT Compiler
In this talk, we will detail our new and generic methods to bypass StructureID Randomization mitigation, which allows an attacker to construct the addrOf/fakeObj primitives and gain the arbitrary Read/Write ability smoothly. Unlike the bug-specifi...
Yong Wang
Security
Detecting (un)Intentionally Hidden Injected Code by Examining Page Table Entries
In this talk, we will cover hiding techniques that prevent executable pages (containing injected code) from being reported by current memory forensic plugins. These techniques can either be implemented by malware in order to hide its injected code...
Frank Block
Security
Chain of Fools: An Exploration of Certificate Chain Validation Mishaps
In this talk, we explore the implications of poor cryptographic API design, how insecure certificate chain validation implementations can be exploited, and how widespread usage of APIs like Android SafetyNet are in certain verticals. We also propo...
James Barclay, Olabode Anise, Nick Mooney
Security
New Exploit Technique In Java Deserialization Attack
In our depth research, we analyzed more than 10000+ Java third-party libraries and found many cases which can be exploited in real-world attack scenarios. In this talk, we will bat around the principle and exploit technique of these vulnerabilitie...
Lucas Zhang, Yongtao Wang, Kunzhe Chai
Java
Security
Simple Spyware: Androids Invisible Foreground Services and How to (Ab)use Them
This simple to implement spyware shows that Androids permission model can't prevent an excessive use of permissions and that the limitations do not prevent the collection of the user's sensitive data. In order to prevent such attacks, it would be ...
Bernhard Tellenbach, Thomas Sutter
Security
Implementing the Lessons Learned From a Major Cyber Attack
In June 2017, Maersk suffered a major notpetya cyber-attack, this session explains lessons learned and how they are now being applied within Maersk. Full Abstract: https://www.blackhat.com/eu-19/briefings/schedule/#implementing-the-lessons-lear...
Andy Powell
Security
Trust in Apple's Secret Garden: Exploring & Reversing Apple's Continuity Protocol
By using protocols like AirDrop, iMessage which falls under the umbrella of "Continuity," devices can seamlessly share messages, browser tabs, clipboards and wireless hotspots without much hassle of setting it up. However, during our daily usage o...
Ta-Lun Yen
Security
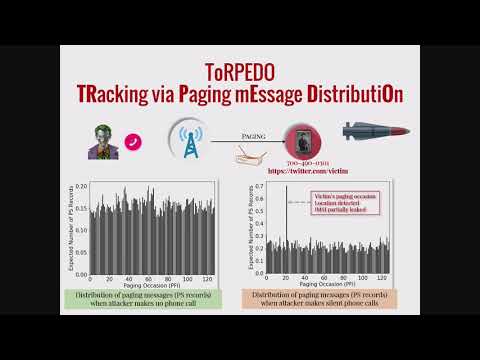
Side Channel Attacks in 4G and 5G Cellular Networks
This talk first presents how the fixed nature of paging occasions can be exploited as a side-channel by an adversary in the vicinity of a victim to associate the victim's soft-identity (e.g., phone number, Twitter handle) with its paging occasion,...
Syed Hussain
Security
Mobile Network Hacking, IP Edition
We explore which protection measures are missing from the mobile network and discuss how to best bring them over from the IT security domain into mobile networks. Full Abstract & Presentation Materials: https://www.blackhat.com/eu-19/briefings/...
Sina Yazdanmehr, Karsten Nohl, Luca Melette
Hacking
Security
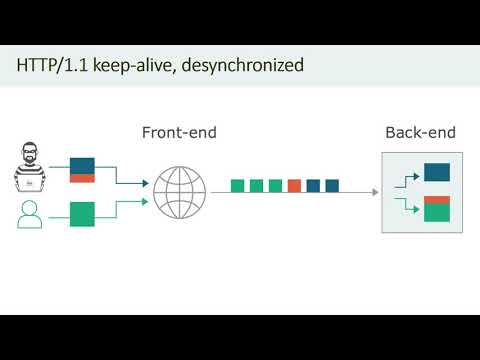
HTTP Desync Attacks: Request Smuggling Reborn
HTTP requests are traditionally viewed as isolated, standalone entities. In this session, I'll introduce techniques for remote, unauthenticated attackers to smash through this isolation and splice their requests into others, through which I was ab...
James Kettle
Security
Reverse Engineering and Exploiting Builds in the Cloud
Continuous Integration, Delivery, and Deployment (CI/CD) and Containers are common terms in today’s IT landscapes and core approaches for modern software development and operation. We will give a short, to-the-point introduction of CI/CD with rega...
Chris Le Roy, Etienne Stalmans, Matthias Luft
Security
Fatal Fury on ESP32: Time to Release Hardware Exploits
This talk presents, in a methodical way, how to defeat one by one the previously listed security features, having physical access to the device and using low-cost hardware techniques such as voltage glitching, analog side-channels, micro-soldering...
Limited Results
Security
Money Doesn't Stink - Cybercriminal Business Insight of A New Android Botnet
This presentation shows the inner relationships of a blackmarket underground attacking group, their daily survival problems, decisions, money and struggles to make a living from malicious activities. How the hierarchy of malware development worked...
María José Erquiaga, Sebastián García, Anna Shirokova
Security