DEF CON 27
Talks
Industry of Social Media Manipulation Driven by Malware
This talk is the grand finale of a four-year long investigation that started with analyzing an IoT botnet, to discovering the structured industry that exists behind social media manipulation (SMM). SMM is the deliberate act of paying for popularit...
Olivier Bilodeau, Masarah Paquet-Clouston
Hacking
How You Can Buy ATT TMobile and Sprint Real Time Location Data
Major US telecommunications companies AT&T, T-Mobile, and Sprint have been quietly selling access to their customers’ real-time location data, including cell tower information as well as highly precise GPS data. Through a complex network of dodgy ...
Joseph Cox
Hacking
GSM We Can Hear Everyone Now
The presentation demonstrates that the security of the A5/1 and A5/3 ciphers used to protect cellular calls are vulnerable to compromise leading to full decryption of GSM communications, using freely available open source solutions along with our ...
Eoin Buckley, Campbell Murray, James Kulikowski
Hacking
DEF CON to help hackers anonymously submit bugs to the government
Here’s the use case. You learn of a problem with a government system or some technology, and you want to do the right thing. You want to get the information into the right hands, but you’d be more comfortable sharing if you knew you couldn’t be id...
Runa Sandvik, Jennifer Granick, Pablo Breuer, Christopher Krebs, Corbin Souffrant
Hacking
Cult of the Dead Cow - Change the World, cDc Style
The Cult of the Dead Cow changed the culture of the entire security industry, the attitude of companies who had ignored risks, and even how the feds dealt with hackers. In this session, four key figures from the group’s first 35 years will cover t...
Deth Vegetable, Chris Dildog Rioux, Joseph Menn, Peiter Mudge Zatko
Hacking
Reverse Engineering 4g Hotspots for Fun, Bugs and Net Financial Loss
“5G is coming” (apparently). That probably means, over the next few years, more and more people are going to be using more and more cellular-connected devices for their day-to-day TCP/IP activities. The problem is, a lot of existing 4G modems a...
g richter
Hacking
Adventures In Smart Buttplug Penetration testing
Analysts believe there are currently on the order of 10 billions Internet of Things (IoT) devices out in the wild. Sometimes, these devices find their way up people's butts: as it turns out, cheap and low-power radio-connected chips aren't just gr...
smealum
Hacking
Confessions of an Nespresso Money Mule
In 2018 I somewhat innocently bought very expensive coffee (Nespresso capsules) online from Ebay. What followed was a series of unexpected additional packages from the manufacturer Nespresso and a lurking suspicion that something had gone terribly...
Nina Kollars
Hacking
I Know What U Did Last Summer - 3 Yrs Wireless Monitoring at DEF CON
For the past 3 years d4rkm4tter has been obsessed with monitoring the wireless networks at DEF CON. This talk will take you on a journey through the successes and failures that lead to the creation of the WiFiCactus and the over 1 TB of data captu...
Mike Spicer
Hacking
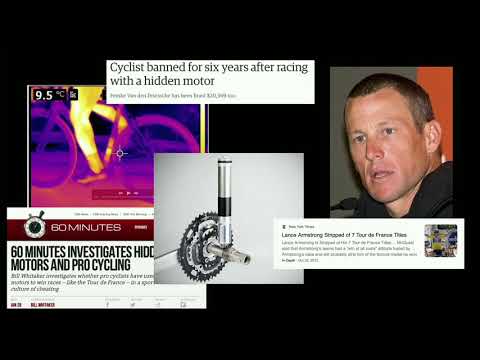
Cheating in eSports How to Cheat at Virtual Cycling
Athletes are competing in virtual cycling by riding real bikes on stationary trainers which power the in-game athletic performance. Riders train and compete online against each other. New racing teams are even competing in Union Cycliste Internati...
Brad Dixon
Hacking
Web2Own Attacking Desktop Apps from Web Security's Perspective
People are always talking about binary vulnerabilities when attacking desktop applications. Memory corruptions are always costly to find. Meanwhile, mitigations introduced by operating systems make them harder to be exploited. More and more applic...
Ce Qin, Jianing Wang, Junyu Zhou
Hacking
Go NULL Yourself
Input sanitization issues will always exist, although it’s surprising at how we’re still seeing amateur mistakes being made on everyday applications and systems used by millions. After making some observations against automatic license plate recog...
Joseph Tartaro
Hacking
Zombie Ant Farm Practical Tips for Playing Hide and Seek
EDR solutions have landed in Linux. With the ever increasing footprint of Linux machines deployed in data centers, offensive operators have to answer the call. In the first part of the talk we will share practical tips and techniques hackers ca...
Dimitry Snezhkov
Hacking
.NET Malware Threats: Internals And Reversing
.NET malware is well-known by security analysts, but even existing many tools such as dnSpy,.NET Reflector, de4dot and so on to make the analysis easier, most professionals have used them as a black box tool, without concerning to .NET internals, ...
Alexandre Borges
.NET
Hacking
MOSE Using Configuration Management for Evil
Configuration Management (CM) tools are used to provision systems in a uniform manner. CM servers are prime targets for exploitation because they are connected with key machines. The tools themselves are powerful from a security standpoint: they a...
Jayson Grace
Hacking
Sound Effects Exploring Acoustic Cyberweapons
While recent research has explored the capability of attacks to cause harm by targeting devices – e.g., SCADA systems, vehicles, medical implant devices - little consideration has been given to the concept of attacks affecting psychological and ph...
Matt Wixey
Hacking
Everything you wanted to know about the DEF CON NOC
It's been a while, something like DEF CON 19, since we had the chance to have more than a few minutes at closing ceremonies to talk to everyone about the DEF CON NOC. It is not uncommon for people during the show or throughout the year to come to ...
DEF CON NOC
Hacking
Owning The Cloud Through Server Side Request Forgery
With how many apps are running in the cloud, hacking these instances becomes easier with a simple vulnerability due to an unsanitized user input. In this talk, we’ll discuss a number of different methods that helped us exfil data from different ap...
Cody Brocious, Ben Sadeghipour
Cloud
Hacking
100 seconds of Solitude Defeating Cisco Trust Anchor
First commercially introduced in 2013, Cisco Trust Anchor module(TAm) is a proprietary hardware security module that is used in a wide range of Cisco products, including enterprise routers, switches and firewalls. TAm is the foundational root of t...
Ang Cui, Jatin Kataria, Rick Housley
Hacking
Apache Solr Injection
Apache Solr is a search platform used by many enterprise companies to add a full text search functionality to their websites. Often hidden behind firewalls, it provides a rich API to search across large datasets. If this API is used by web applica...
Michael Stepankin
Hacking
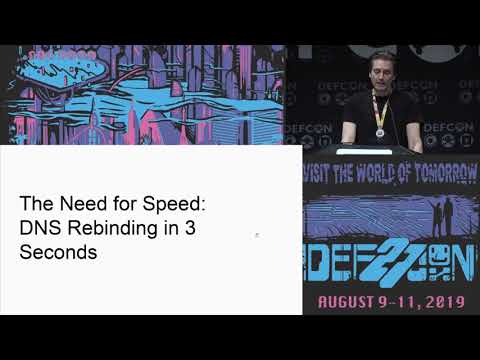
State of DNS Rebinding Attacks & Singularity of Origin
Do you want to know how you can exploit DNS rebinding 10x faster, bypass prevention mechanisms, interactively browse the victim's internal network, and automate the whole process during your next red team exercise? This talk will teach you how ...
Roger Meyer, Gerald Doussot
Hacking
Vacuum Cleaning Security Pinky and The Brain Edition
Data collected by vacuum cleaning robot sensors is highly privacy-sensitive, as it includes details and metadata about consumers’ habits, how they live, when they work or invite friends, and more. Connected vacuum robots are not as low-budget as o...
Jiska, Fabian Ullrich
Hacking
SELECT code execution from using SQlite
Everyone knows that databases are the crown jewels from a hacker's point of view, but what if you could use a database as the hacking tool itself? We discovered that simply querying a malicious SQLite database - can lead to Remote Code Execution. ...
Omer Gull
Hacking
Bugfinding & Exploit Techniques Android File Transfer Apps
Nearby sharing apps are very convenient and fast when you want to transfer files and have been pre-installed on billions of devices. However, we found that most of them will also open a door for attackers to steal your files and even more. Firs...
Huiming Liu, Xiangqian Zhang
Android
Hacking
Defeating Bluetooth Low Energy 5 PRNG for Fun and Jamming
Bluetooth Low energy version 5 has been published in late 2016, but we still have no sniffer supporting this specific version (and not that much compatible devices as well). The problem is this new version introduces a new channel hopping algorith...
Damien Cauquil
Hacking
HTTP Desync Attacks: Smashing into the Cell Next Door
HTTP requests are traditionally viewed as isolated, standalone entities. In this session, I'll introduce techniques for remote, unauthenticated attackers to smash through this isolation and splice their requests into others, through which I was ab...
James Kettle
Hacking
Firmware Slap Automating Discovery - Exploitable Vulns
DARPA’s Grand Cyber Challenge foretold an ominous future stricken with machines exploiting our code and automatically compromising our systems. Today, we have the chance to steel ourselves by creating new hope through stronger tools and techniques...
Christopher Roberts
Hacking
Duplicating Restricted Mechanical Keys
Secure facilities in North America use lock systems like Medeco, Abloy, Assa and Mul-T-Lock partly to resist lock picking, but also to prevent the duplication and creation of unauthorised keys. Places such as the White House and the Canadian Parli...
Bill Graydon, Robert Graydon
Hacking
HVACking Understand the Delta Between Security and Reality
Like most modern devices, building controllers have increasingly become network connected, exposing them to a wider range of threats. If malicious actors could manipulate access control systems, boiler rooms, or temperature control for critical in...
Douglas McKee, Mark Bereza
Hacking
The Ether Wars Exploits counter exploits and honeypots
Ethereum smart contracts are Turing-complete programs that mediate transfers of money. It doesn't come as a surprise that all hell is breaking loose on the Ethereum blockchain. In this talk, we'll introduce Karl, an Ethereum blockchain monitor,...
Bernhard Mueller, Daniel Luca
Crypto
Hacking
Intro to Hardware Hacking
From small business to large enterprise, VOIP phones can be found on nearly every desk. But how secure are they? What if your phone was spying on every conversation you have? This talk is an introduction to hardware hacking and as a case study ...
Philippe Laulheret
Hacking
Please Inject Me, a x64 Code Injection
Malware authors are always looking for new ways to achieve code injection, thereby allowing them to run their code in remote processes. Code Injection allows hackers to better hide their presence, gain persistence and leverage other processes’ dat...
Alon Weinberg
Hacking
Backdooring Hardware by Injecting Malicious Payloads
Is targeting microcontrollers worth the effort? Nowadays, they are responsible for controlling a wide range of interesting systems, e.g., physical security systems, car’s ECUs, semaphores, elevators, sensors, critical components of industrial syst...
Sheila Ayelen Berta
Hacking
Panel - Hacking Congress The Enemy Of My Enemy Is My Friend
A SIMULATED crisis is unfolding on a national scale, based loosely on the NotPetya attack of 2017. Triggered by a yet-unknown adversary, what started as a an isolated technical issue has quickly escalated into a society-wide event affecting millio...
James Langevin, Jen Ellis, Jane Harman, Cris Thomas, Ted Lieu
Hacking
Breaking Google Home Exploit It with SQLite
Over the past years, our team has used several new approaches to identify multiple critical vulnerabilities in SQLite and Curl, two of the most widely used basic software libraries. These two sets of vulnerabilities, which we named "Magellan" and ...
YuXiang Li, Wenxiang Qian, HuiYu Wu
Hacking
SQLite
Hacking Your Thoughts Batman Forever meets Black Mirror
Companies are coming for your brains. The electricity in your brains, to be more precise. Valve, Facebook, Elon Musk and more are funding research into technologies that will translate neural signals into controls for devices like computers, smart...
Katherine Pratt
Hacking
MI CASA SU CASA My 192.168.1.1 is Your 192.168.1.1
Your browser thinks my 192.168.1.1 is the same as your 192.168.1.1. Using a novel combination of redirects, Karma, JavaScript and caching we demonstrate that it’s viable to attack internal management interfaces without ever connecting to your netw...
Elliott Thompson
Hacking
EDR is Coming Hide Yo Sh!t
There’s a new, largely unaddressed threat in the security industry today, Endpoint Detection and Response (EDR), which aims to stop threat actors in their tracks. The scenario plays out like this... At first your campaign is going well and your at...
Michael Leibowitz, Topher Timzen
Hacking
JOP ROCKET A Wicked Tool for JOP Gadget Discovery
Return-oriented Programming (ROP) has been the predominate code-reuse attack for over a decade, but there are other options. Many mitigations can detect ROP due to heuristics, but these fail to detect Jump-oriented Programming (JOP). The JOP ROCKE...
Bramwell Brizendine, Joshua Stroschien
Hacking
Poking the S in SD Cards
Ever wonder why the S in SD cards stands for Secure? Well, it turns out that it is possible to read and/or write protect these cards by software using specific commands. As you might expect, this process isn’t as "secure" as the name implies leadi...
Nicolas Oberli
Hacking
Relaying Credentials has Never Been Easier
Active Directory has always been a popular target for attackers, with a constant rise in attack tools attempting to compromise and abuse the main secrets storage of the organization. One of the weakest spots in Active Directory environments lies i...
Marina Simakov, Yaron Zinar
Hacking
Information Security in the Public Interest
Computer security is now a public policy issue. Election security, blockchain, "going dark," the vulnerabilities equities debate, IoT safety , data privacy, algorithmic security and fairness, critical infrastructure: these are all important public...
Bruce Schneier
Hacking
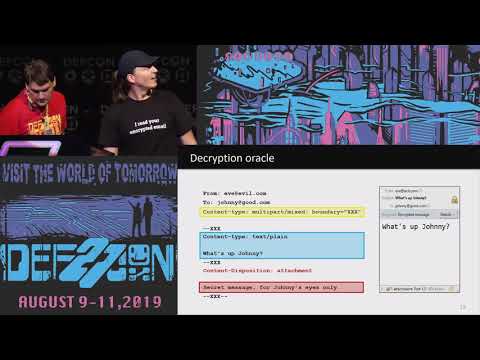
Covert Attacks on Email End-to-End Encryption
We show practical attacks against OpenPGP and S/MIME encryption and digital signatures in the context of email. Instead of targeting the underlying cryptographic primitives, our attacks abuse legitimate features of the MIME standard and HTML, as s...
Jens Muller
Hacking
HAKC THE POLICE
PULL OVER! No, it is a cardigan, but thanks for noticing! After getting a nasty speeding ticket, OG SecKC HA/KC/ER hevnsnt decided enough was enough, and set out to fully understand police speed measurement devices, and develop homebrew counterme...
Bill Swearingen
Hacking
How To Improve Coverage Guided Fuzzing Find New 0days
Fuzzing remains to be the most effective technique for bugs hunting in memory-unsafe programs. Last year, hundreds of security papers and talks on fuzzing have been published and dozens of them were focused on adapting or improving American Fuzzy ...
Maksim Shudrak
Hacking
Unpacking Pkgs - A Look Inside MacOS Installer Packages
We are hackers, we won't do as you expect or play by your rules, and we certainly don't trust you. JAR files are really ZIPs...unzip them! So are Microsoft's DOCX, XLSX, PPTX, etc. Let's open them up! macOS applications (.app "files") are really d...
Andy Grant
Hacking
Key Search Attacks Against Modern Symmetric Ciphers
In theory, brute force key recovery attacks against modern ciphers like AES should be impractical with the current state of computer hardware. It's often said that recovering an AES key should take longer than the remainder of the life of the sun....
Daniel Pagan, Daniel Crowley
Hacking
Are Quantum Computers Really A Threat To Cryptography?
Shor's Algorithm for factoring integer numbers is the big threat to cryptography (RSA/ECC) as it reduces the complexity from exponential to polynomial, which means a Quantum Computer can reduce the time to crack RSA-2048 to a mere 10 seconds. Howe...
Andreas Baumhof
Hacking
The ABC of Next Gen Shellcoding
Shellcodes are short executable stubs that are used in various attack scenarios, whenever code execution is possible. After briefly recalling how they work in general and what interesting things they can do, besides obviously running a reverse-she...
Georges-Axel Jaloyan, Rémi Géraud-Stewart, Hadrian Barral
Hacking
Rise of the Hypebots Scripting Streetwear
Buying Supreme is even harder when most of your competitors are AI. The era of bot purchasing has arrived and more often than not, purchasing shoes, shirts, and swag, requires shell scripting. We will look at how simplistic (and how complicated) p...
finalphoenix
Hacking
Breaking the Back End - Sometimes it's Just Bad Design
Reverse engineering is critical to exploitation. However, going through the process of reverse engineering can often lead to a great deal more than just uncovering a bug. So much so that you might find what you need for exploitation even if you do...
Gregory Pickett
Hacking
Phreaking Elevators
This is a comprehensive dive into the current emergency phones with an in-depth look at the phones used in elevators. This talk will provide unique insight into a topic that hasn't been covered before: Elevator Phones. During this talk, I will dis...
Will Caruana
Hacking
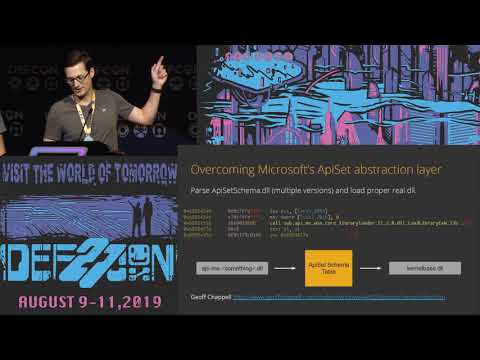
Get Off the Kernel if You Can't Drive
For software to communicate with hardware, it needs to talk to a kernel-mode driver that serves as a middle-man between the two, helping to make sure everything operates as it should. In Windows that is done using the Kernel-Mode Driver Framework ...
Mickey Shkatov, Jesse Michael
Hacking
Malproxy Leave Your Malware at Home
During a classic cyber attack, one of the major offensive goals is to execute code remotely on valuable machines. The purpose of that code varies on the spectrum from information extraction to physical damage. As defenders, our goal is to detect a...
Amit Waisel, Hila Cohen
Hacking
Help Me Vulnerabilities You're My Only Hope
MikroTik routers keep getting owned. They’ve been exploited by advanced threats like VPNFilter, Slingshot APT, and Trickbot. They’ve been compromised by coin miners, botnets, and who knows what else. With each new campaign the security industry pu...
Jacob Baines
Hacking
Meticulously Modern Mobile Manipulations
Mobile app hacking peaked in 2015 with tools like keychain-dumper & ssl-kill-switch released but requiring jailbroken/rooted devices. Back then, wresting the power to understand & modify apps on our devices from dystopian looking mega corps was ou...
Leon Jacobs
Hacking
Are Your Child's Records at Risk - The Current State of School
From credit reporting agencies to hotel enterprises, major data breaches happen daily. However, when was the last time we considered the data security of children and middle-level education students? The infosec community spends so much time think...
Bill Demirkapi
Hacking
Hacking WebAssembly Games with Binary Instrumentation
WebAssembly is the newest way to play video games in your web browser. Both Unity3d and Unreal Engine now support WebAssembly, meaning the amount of WebAssembly games available is growing rapidly. Unfortunately the WebAssembly specification is mis...
Jack Baker
Hacking
WebAssembly
Infiltrating Corporate Intranet Like NSA Preauth RCE
Computer security is now a public policy issue. Election security, blockchain, "going dark," the vulnerabilities equities debate, IoT safety , data privacy, algorithmic security and fairness, critical infrastructure: these are all important public...
Tingyi Chang, Cheng-Da Tsai
Hacking
Why You Should Fear Your mundane Office Equipment
The security of common enterprise infrastructure devices such as desktops and laptops has advanced over the years through incremental improvements in operating system and endpoint security. However, security controls for network devices such as en...
Mario Rivas, Daniel Romero
Hacking
Tag side attacks against NFC
This talk covers tag-side attacks against NFC communication protocols, including cracking of Mifare encryption keys and performing targeted attacks against NFC readers. In addition, it will cover the design and creation of devices capable of emula...
Christopher Wade
Hacking
The Tor Censorship Arms Race The Next Chapter
Tor is a free-software anonymizing network that helps people around the world use the Internet in safety. But who cares how good Tor's privacy is, if your government prevents you from reaching the Tor network? In the beginning, some countries f...
Roger Dingledine
Hacking
Your Car is My Car
For many of us, our cars are one of the largest purchases we will ever make. In an always connected world it is natural that we would want to have the convenience of being able to remotely monitor our vehicles: to do everything from remind ourselv...
Jmaxxz
Hacking
Don't Red Team AI Like a Chump
AI needs no introduction as one of the most overhyped technical fields in the last decade. The subsequent hysteria around building AI-based systems has also made them a tasty target for folks looking to cause major mischief. However, most of the p...
Ariel Herbert-Voss
Hacking
Exploiting Qualcomm WLAN and Modem Over the Air
In this talk, we will share our research in which we successfully exploit Qualcomm WLAN in FIRMWARE layer, break down the isolation between WLAN and Modem and then fully control the Modem over the air. Setup the real-time debugger is the key. W...
Xiling Gong, Peter Pi
Hacking
Exploiting Windows Exploit Mitigation for ROP Exploits
“A concept is a brick. It can be used to build a courthouse of reason. Or it can be thrown through the window.” ― Gilles Deleuze Ever since Smashing the Stack For Fun And Profit was published by Aleph One almost a quarter century ago the securi...
Omer Yair
Hacking
HackPac Hacking Pointer Authentication in iOS User Space
Pointer Authentication (in short, PAuth) is the latest security mechanism in iOS. It is proposed to protect the integrity of pointers with hardware-assisted encryption, thus eliminating the threats of code-reuse attacks. In PAuth, a cryptographic ...
Xiaolong Bai, Min Zheng
Hacking
iOS
Can You Track Me Now
Amidst the current public outcry about privacy abuses by corporate america, one sector has received far less scrutiny than it deserves: phone companies. America’s phone companies have a hideous track record on privacy. During the past two decades,...
Ron Wyden
Hacking
Next Generation Process Emulation with Binee
The capability to emulate x86 and other architectures has been around for some time. Malware analysts have several tools readily available in the public domain. However, most of the tools stop short of full emulation, halting or doing strange thin...
Kyle Gwinnup, John Holowczak
Hacking
SDR Against Smart TVs URL Channel Injection Attacks
Software-defined-radio has revolutionized the state of the art in IoT security and especially one of the most widespread devices: Smart TV. This presentation will show in detail the HbbTV platform of Smart TV, to understand and demonstrate two att...
Pedro Cabrera Camara
Hacking
Process Injection Techniques Gotta Catch Them All
When it comes to process injection in Windows, there are only 6-7 fundamental techniques, right? Wrong. In this talk, we provide the most comprehensive to-date “Windows process injection” collection of techniques. We focus on Windows 10 x64, and o...
Itzik Kotler, Amit Klein
Hacking
Harnessing Weapons of Mac Destruction
Whenever a new Mac malware specimen is uncovered, it provides a unique insight into the offensive Mac capabilities of hackers or nation-state adversaries. Better yet, such discoveries provide fully-functional capabilities that may be weaponized fo...
Patrick Wardle
Hacking
Mac
Im on Your Phone Listening Attacking VoIP Config Interfaces
If toasters talking to fridges is no joke to you, then you are aware of the big Internet of Things hype these days. While all kind of devices get connected and hacked, one of the oldest class of IoT devices seems to be forgotten even though it is ...
Philipp Roskosch, Stephan Huber
Hacking
Surveillance Detection Scout Your Lookout on Autopilot
Surveillance detection routes are a daily occurrence for clandestine operatives and agents all over the world. These mentally taxing counter-surveillance measures often mean the difference between life and death. Surveillance Detection Scout hopes...
Truman Kain
Hacking
No Mas How Side Channel Flaw Opens ATM Pharmacies and Gov to Attack
Hacking ‘high security’ electronic locks has become a bit of a hobby, but what if you identify an unpatchable design pattern that unlocks buckets of cash and government secrets? How long do wait before telling ‘people’? let’s talk about how these ...
Mike Davis
Hacking
Want Strong Isolation Just Reset Your Processor
Today's systems sandbox code through traditional techniques: memory protection and user-kernel mode. Even high-security devices like hardware cryptocurrency wallets use such an architecture. Unfortunately, this arrangement has a history of securit...
Anish Athalye
Hacking
Evil eBPF Practical Abuses of In-Kernel Bytecode Runtime
eBPF (or "extended" Berkeley Packet Filter) is a bytecode instruction set and virtual machine used as a safe computing environment within the Linux kernel to perform arbitrary programmatic actions. It is a redesign of Linux's original in-kernel BP...
Jeff Dileo
Hacking
Weaponizing Hypervisors to Beat Car and Medical Device Attacks
Historically, hypervisors have existed in the cloud for efficient utilization of resources, space, and money. The isolation feature is one of the reasons hypervisors are heavily moving to other ecosystems, like Automobiles, so that for example, if...
Ali Islam, Dan Regalado
Hacking
RACE - Minimal Rights and ACE for Active Directory Dominance
User rights and privileges are a part of the access control model in Active Directory. Applicable only at the local computer level, a user generally has different rights (through access tokens) on different machines in a domain. Another part of th...
Nikhil Mittal
Hacking
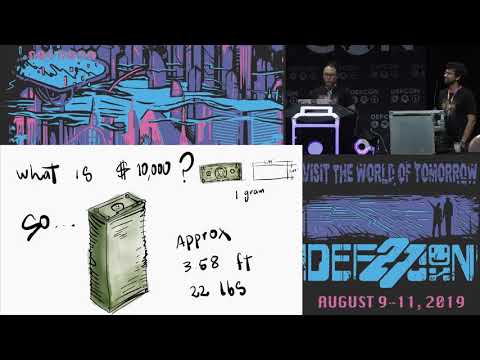
Behind the Scenes of the DEF CON 27 Badge
Incorporating natural elements, complex fabrication techniques, and components rarely seen by the outside world, the DEF CON 27 Badge brings our community together through Technology's Promise. Join DEF CON's original electronic badge designer Joe...
Joe Grand
Hacking
Deep Learning - Revolutionizing Side Channel Cryptanalysis
This talk explores how AI is revolutionizing hardware side-channel attacks and what this new wave of attacks mean for the future of hardware cryptography. Based on the lessons learned while successfully attacking many hardware AES implementations ...
Elie Bursztein, Jean Michel Picod
Hacking
Machine Learning
SSO Wars: The Token Menace
It is the year 2019. Humanity has almost won its long-standing war against Single-Sign On (SSO) bugs. The last of them were discovered and eradicated some time ago and the world is now living in an era of prosperity while the Auth Federation enjoy...
Oleksandr Mirosh, Alvaro Muñoz
Hacking
Say Cheese How I Ransomwared Your DSLR Camera
It's a nice sunny day on your vacation, the views are stunning, and like on any other day you take out your DSLR camera and start taking pictures. Sounds magical right? But when you get back to your hotel the real shock hits you: someone infected ...
Eyal Itkin
Hacking
All the 4G Modules Could Be Hacked
Nowadays more and more 4G modules are built into IoT devices around the world, such as vending machines, car entertainment systems, laptops, advertising screens, and urban cameras etc. But no one has conducted a comprehensive security research on ...
Zheng Huang, Gao Shupeng
Hacking
API Induced SSRF How ApplePay Scattered Vulns Across the Web
The 2016 WWDC saw the dawn of Apple Pay Web, an API that lets websites embed an Apple Pay button within their web-facing stores. Supporting it required a complex request flow, complete with client certificates and a custom session server. This pro...
Joshua Maddux
Hacking
Finding Secrets in Publicly Exposed Ebs Volumes
Did you know that Elastic Block Storage (Amazon EBS) has a "public" mode that makes your virtual hard disk available to anyone on the internet? Apparently hundreds of thousands of others didn't either, because they're out there exposing secrets fo...
Ben Morris
AWS
Hacking
Im In Your Cloud Pwning Your Azure Environment
After having compromised on-premise for many years, there is now also the cloud! Now your configuration mistakes can be accessed by anyone on the internet, without that fancy next-gen firewall saving you. With this talk I’ll share my current resea...
Dirk-jan Mollema
Azure
Hacking
Reverse Engineering 17+ Cars in Less than 10 Minutes
Brent provides a live demonstration reversing engineering 17 or more unknown passenger vehicle CAN networks in under 10 minutes using new automated techniques. These unsupervised techniques are over 90% accurate and consistent when tested using pr...
Brent Stone
Hacking