OWASP BeNeLux Day 2017
Talks
Common REST API security pitfalls
The shift towards a REST API landscape indicates a significant evolution in the way we build applications. The rise of JavaScript and mobile applications have sparked an explosion of easily-accessible REST APIs. But how do you protect access to yo...
Philippe De Ryck
How to spend $3.6mil on one coding mistake
In a recent global study, the average cost of a data breach is $3.62M globally. This session will discuss infamous examples of data breaches that has made headlines around the world. We will explore the technical details of the vulnerability itsel...
Matias Madou
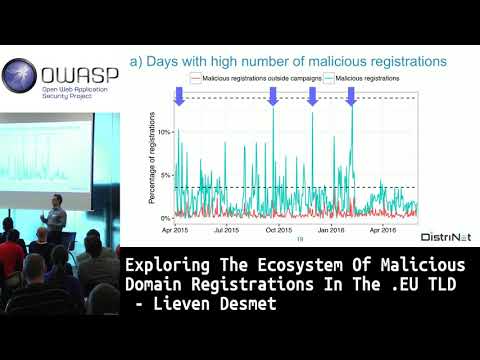
Exploring the ecosystem of malicious domain registrations in the .eu TLD
In this talk, we report on an extensive analysis of 14 months of domain registration in the .eu TLD. The purpose is to identify large-scale malicious campaigns. Overall, the dataset of this study contains 824,121 new domain registrations; 2.53% of...
Lieven Desmet
Creating An AppSec Pipeline With Containers In A Week
Join us on our adventure of setting up a appsec pipeline with Docker containers. What did go wrong, how did we succeed? How do you fight false positives and how do you get the best out of the products out there without bothering the development te...
Jeroen Willemsen
Docker
The evil friend in your browser
On the one hand, browser extensions, e.g., for Chrome, are very useful, as they extend web browsers with additional functionality (e.g., blocking ads). On the other hand, they are the most dangerous code that runs in your browsers: extension can r...
Achim D. Brucker
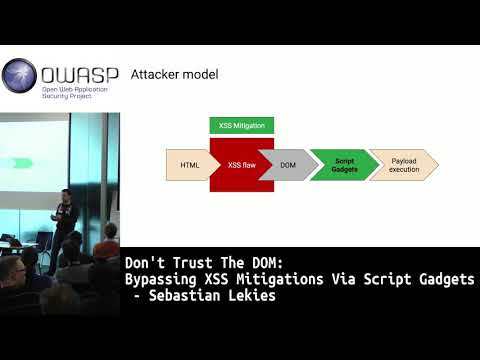
Don't trust the DOM: Bypassing XSS mitigations via script gadgets
Cross-Site Scripting is a constant problem of the Web platform. Over the years many techniques have been introduced to prevent or mitigate XSS. Most of these techniques, thereby, focus on script tags and event handlers. HTML sanitizers, for exampl...
Sebastian Lekies
A Series of Unfortunate Events: Where Malware Meets Murphy
When an end user reports some "strange looking file names", which, after investigating, you discover include several hundreds of Gigabytes of encrypted data, you of course know you are going to have a bad day. Your AV solution has failed you, your...
Mattijs van Ommeren