AppSec California 2018
Talks
Seeing Through the Fog - Navigating the Security Landscape of a Cloud-First World
The prospect of the cloud is extremely attractive to many enterprises, so it’s no surprise that several industries are in an all out sprint to get there. Cloud has become so popular that many CIOs have simply been given the directive “get to the c...
Ben Johnson
The Path Of DevOps Enlightenment For InfoSec
Security as we have known it has completely changed. Through challenges from the outside and from within there is a wholesale conversion happening across the industry where DevOps and Security are joining forces. This talk is a hybrid of inspirati...
James Wickett
OWASP Top 10
OWASP Top 10 Andrew is an in demand speaker and trainer, with past speaking engagements at AusCERT, linux.conf.au, Black Hat, OWASP AppSec EU and AppSec USA, and training many thousands of developers and information security professionals throu...
Andrew van der Stock
Edgeguard: Client-side DOM Security - detecting malice - An Open Framework
“Project edgeguard” is a open framework that allows you to detect when malicious content (planted in your browser via hacking or client-side malware attacks) results in sensitive user data to be stolen and transmitted to third parties (hackers, ...
Eoin Keary
Security After Death -- Not your problem, or is it?
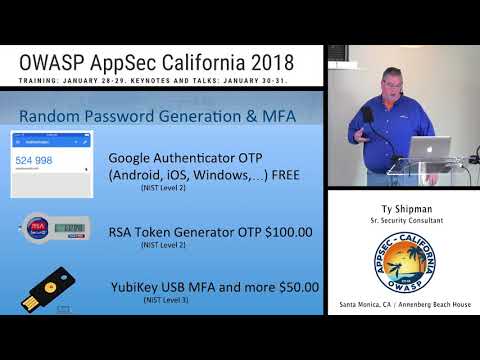
The talk covers practical solutions to storing passwords and secure ways to share those passwords. The solutions range from commercial to open source and even some roll your own. It will also cover solutions that answer the question; “How do I ...
Ty Shipman
DevOps Is Automation, DevSecOps Is People
A lot of appsec boils down to DevOps ideals like feedback loops, automation, and flexibility to respond to situations quickly. DevOps has the principles to support security, it should have to knowledge and tools to apply it. Real-world appsec deal...
Mike Shema
Decrease Your Stress and Increase Your Reach with Appsec Champions
Being the only person in the entire company who works the appsec program gets old. You're getting no help from anyone and no one cares about what you're doing. Are you the ONLY PERSON who actually cares about security? Are you even making a differ...
Coleen Coolidge
The Bug Hunter's Methodology 2.0
Building on the Bug Hunter's Methodology 1.0 given at Defcon 23, 2.0 brings the newest testing techniques, tools, and vulnerability data to penetration testers and security folk. Dive into new-school advents in discovery, XSS, server-side template...
Jason Haddix
We Come Bearing Gifts: Enabling Product Security with Culture and Cloud
What would it look like if security never had to say “no”? This talk explores that counter-intuitive premise, and shows how it is not just possible but *necessary* to discard many traditional security behaviors in order to support modern high-v...
Patrick Thomas, Astha Singhal
Predicting Random Numbers in Ethereum Smart Contracts
Smart contracts are not only about ICOs - various lotteries, roulettes and card games are implemented in Solidity and can be played by anyone on the Ethereum blockchain. Autonomy of the blockchain limits the sources of entropy for random number ge...
Arseny Reutov
Crypto
Threat Modeling Toolkit
Threat Modeling is a great way to analyze security early in software development by structuring possible attacks, bad actors and countermeasures over a broad view of the targeted system. This talk will describe basic components of a threat model a...
Jonathan Marcil
Pack your Android: Everything you need to know about Android Boxing
Android malware authors may enforce one or a combination of protection techniques like obfuscators, packers and protectors. This additional step just before publishing the app adds complexity for Android Bouncers and various static, and dynamic co...
Swapnil Deshmukh
Android
Women In Security Panel
Women In Security Panel Coleen Coolidge Coleen Coolidge is Head of Security at Segment in San Francisco. Previously, she was at Twilio as Sr Director of Trust and Security. She's also served in security-leadership positions at more traditional...
Coleen Coolidge, Caroline Wong, Magen Wu, Kayva Pearlman, Christina Kubecka
Hunter – Optimize your Pentesters Time
Is your pentest report filled with low risk items? Are these projects that you pentest too short for a full-fledged secure SDLC process or are they third party systems that you have little control over? We at eBay had a similar problem wherein mo...
Kiran Shirali
Unpoisoned Fruit: Seeding Trust into a Growing World of Algorithmic Warfare
Artificial Intelligence, or even just Machine Learning for those who prefer organic, is influencing nearly all aspects of modern digital life. Whether it be financial, health, education, energy, transit...emphasis on performance gains and cost red...
Davi Ottenheimer
MarkDoom: How I Hacked Every Major IDE in 2 Weeks
JavaScript (and HTML) has completely conquered the Web, and now it’s taking over the Desktop. In order to provide more user-friendly graphical interfaces, today's software applications are being built with embedded browsers. Companies such as GitH...
Matt Austin
Where, how, and why is SSL traffic on mobile getting intercepted?
Over the last two years, we've received and analyzed more than ten million SSL validation failure reports from more than a thousand of iOS and Android apps available on the Stores, and used all around the world. From mobile banking to music apps, ...
Alban Diquet
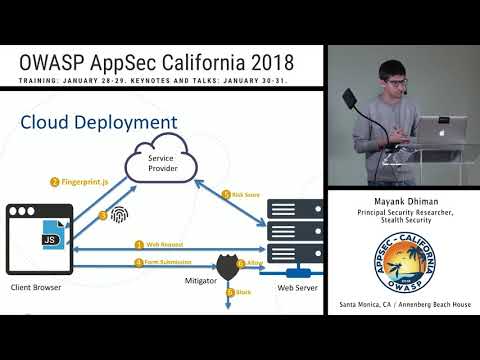
Breaking Fraud and Bot Detection Solutions
Browser fingerprinting and user behavior tracking are powerful techniques used by most fraud and bot detection solutions. These are implemented as JavaScript snippets running the user browser. In this presentation, we’ll demystify what kind of sig...
Mayank Dhiman
Applied Deception Beyond the Honeypot: Moving Past 101
Conflict in cyberspace moves quickly, is primarily asynchronous and can be carried out by a broad range of centralized and decentralized adversaries with great effectiveness. There are many nuanced aspects to this field that make playing defense d...
Robert Wood
Opening Keynote - Flipping the script: Fighting Advanced Threats at their Software Roots
For almost two decades, software security practitioners have successfully defined advanced techniques and tools that can effectively be applied to develop secure software. Yet, all recent major security breaches can be linked to a software vulnera...
Eric Baize
Costs of Coding to Compliance
The problem with most compliance, such as PCI, is that when you manage a project, design, or code only to the line of compliance, there are going to be security gaps. When you have gaps, your risk gets higher, and it becomes more costly to fill th...
Magen Wu
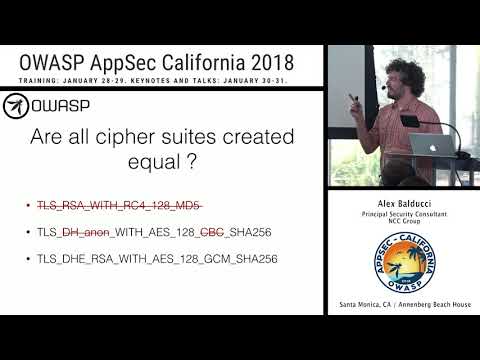
What's New in TLS 1.3
TLS 1.3 is just about here ! This talk will cover the more notable attacks against prior versions of TLS and examine their applicability to TLS 1.3. In doing so, important security related design decisions of TLS 1.3, which thwart these attacks, w...
Alex Balducci
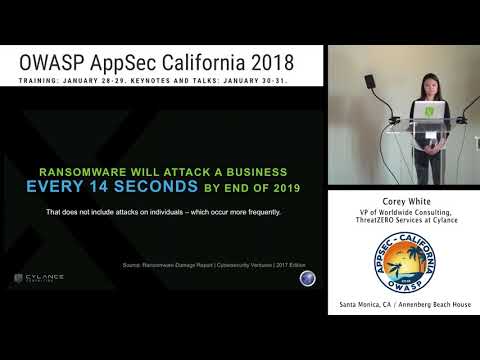
Prevention as a Business Strategy
The world of cybersecurity has changed. Cybercriminals target organizations and unleash a torrent of malicious files and attacks that flood an enterprise until a breach occurs. Many businesses, whether small or large, have been infiltrated and emp...
Corey White
Architecting for Security in the Cloud
The best part about creating new products and services in the cloud is the agility that it provides. Your company literally can scale at the click of a button. But if you take the simplicity of the cloud for granted, you wind up with brittle secur...
Josh Sokol
The Best Flaw Didn't Make Into Production
Security practitioners - the Sisyphus of information technology. We stand with a huge mass of developers creating new content every day, and we trust the training that we offer them, our own abilities as subject matter experts, in the tools we cre...
Izar Tarandach
ReproNow - Save time Reproducing and Triaging Security Bugs
Crowdsourcing security aka Bug Bounty Programs are adapted by almost all companies today: big, small, mid size. While companies reap a lot of benefits, the challenge is to have a security engineer/engineers reproduce each of the bug, understand th...
Lakshmi Sudheer, Vinayendra Nataraja
Leveraging Cloud SDNs to Solve OWASP Top Ten
Historically, implementing network security controls within a virtualized cloud environment have been difficult to implement requiring tricky networking and hypervisor integration. Advancements in software-defined networking (SDN) now allow virtua...
John Studarus
How Privacy Violations, Fines and Economic Sanctions Create Darker Opportunities
Welcome to 2018. Although there’s no flying car in every garage yet. We do have malicious code capable of crashing governments and markets easily available by Google. A world where data seems leaked more often than secured. New laws and fines appe...
Christina Kubecka
Closing Keynote - A free, fair and open internet is a process, not a product
We're never going to be finished with the great work of securing the internet, and we will never be finished with the great work of making sure that it is a force for freedom, privacy, human rights and human flourishing. These are processes, not...
Cory Doctorow
Threat Modeling Panel
Moderated by: Haral Tsitsivas, Software Sr Principal Engineer, Dell EMC Speakers: Jonathan Marcil, Application Security Engineer at Twitch Brook Schoenfield, Principal Architect Product Security at McAfee Adam Shostack, Consultant Izar Tar...
Brook Schoenfield, Jonathan Marcil, Izar Tarandach, Adam Shostack, Haral Tsitsivas
A Tour of API Underprotection
Effective API protection is a growing concern, reflecting the popularity of RESTful Web APIs and richer front-end clients which stress current security and access authorization approaches. You’ll learn about potential threats resulting from unders...
Skip Hovsmith
Robots with Pentest Recipes
Application Security (AppSec) Teams are usually short-staffed. While this is no surprise in itself. Now there’s the added impetus of continuous delivery of security solutions for the continuous delivery pipelines of myriad engineering teams within...
Abhay Bhargav
Opening Keynote: Prove It! Confronting Security With Data
What would you see occurring that would let you know that your security capabilities are improving while the business scales? Scale meaning more staff, more systems, more software, more cloud platforms/apis, more third parties and more regions/mar...
Richard Seiersen
Taking on the King: Killing Injection Vulnerabilities
How do we dismantle the reign of dangerous and prevalent vulnerabilities? "Injection" has crowned the OWASP Top 10 since 2010, while cross-site scripting (a type of injection) has maintained placement in the top four since 2003. If these two vulne...
Justin Collin
Closing Keynote - Digital Disease: How Healthcare Cybersecurity Challenges Can Claim -or Save- Lives
Old “data security first” and HIPAA compliance paradigms in healthcare can’t address the patient safety concerns of a hyper-connected healthcare future built (currently) on the back of insecure software. Healthcare devices and infrastructure are g...
Christian Dameff
European Vacation: Leveraging GDPR for Security
Our friends across the pond, love their privacy. Makes you wonder what they're up to, huh? While many organizations are dreading achieving and maintaining GDPR compliance, if approached properly, it can be a big win for the security of your applic...
Anthony Trummer
GDPR
Authentication Without Authentication
Authentication is important, but how do you authenticate when user interaction is not an option? For example, an IoT app without a user interface. We need to authenticate the app ― without any predefined credentials. But how? Join this session to ...
Omer Levi Hevroni
The Only Reason Security Really Matters for DevOps
This talk begins by exploring the answer to the question, why does DevOps matter? Business do what they need to do to survive and succeed. If their customers need agility, then they will evolve to accommodate that. Next, key differences between...
Caroline Wong
SecDevOps: Current Research and Best Practices
SecDevOps: Current Research and Best Practices Clint Gibler is a senior security consultant and research director at NCC Group, a global information assurance specialist providing organizations with security consulting services. Clint has spoke...
Clint Gibler
Lessons From The Threat Modeling Trenches
What wisdom percolates from building threat modeling practices across 4 organizations? This presentation is drawn from hundreds of students, years of coaching, 100 formal trainings, and 1000’s of threat models. This presentation draws upon experie...
Brook Schoenfield