AppSec California 2019
Talks
The Call is Coming From Inside the House: Lessons in Securing Internal Apps
Locking down internal apps presents unique and frustrating challenges for appsec teams. Your organization may have dozens if not hundreds of sensitive internal tools, dashboards, control panels, etc., running on heterogenous technical stacks with ...
Hongyi Hu
Behind the Scenes: Securing In-House Execution of Unsafe Third-Party Executables
So you want to run FFMpeg or ImageMagick or any other third-party processing library inside your Production environment, and still hope for a good night’s sleep? In-house third-party code execution has its unique set of security challenges. One...
Mukul Khullar
Node.js and NPM Ecosystem: What are the Security Stakes?
NPM and the Node.js ecosystem have vastly changed the way modern software is built. Today, everyone use these tools. The real question is: "how is security handled in that ecosystem?". Vladimir is one of the key individual in this ecosystem an...
Vladimir de Turckheim
Node.js
Contact Center Authentication
You've built login for your application—maybe you even have 2FA—but what happens when a customer calls the support number listed on your website or product? Security teams and app developers have thought a lot about online authentication, but w...
Kelley Robinson
Browser fingerprints for a more secure web
Browser fingerprints can be used to invade users' privacy by tracking them across websites. But they can also be used to protect users against account takeovers. At Salesforce, we have successfully deployed browser fingerprints to detect session r...
Julien Sobrier, Ping Yan
On the Frontlines: Securing a Major Cryptocurrency Exchange
The high transaction speed, lack of traceability, and multi-national nature of cryptocurrencies make them prime targets for small-time thieves and well-financed attackers alike. As such, cryptocurrency exchanges continually face a barrage of websi...
Neil Smithline
Crypto
Creating Accessible Security Testing with ZAP
Intoducing security testing tools to a QA or developers workflow can be difficult when the tools aren't easy or intuitive to use. Even for security professionals, the friction of cumbersome security tooling can prevent them from getting the most f...
David Scrobonia
BoMs Away - Why Everyone Should Have a BoM
The benefits of using third-party and open source components are often negated by the inherent risks that come with them. Systematically reducing risk while allowing the benefits to prevail can be challenging. Organizations often rely on methods o...
Steve Springett
Pose a Threat: How Perceptual Analysis Helps Bug Hunters
Every picture I take, I pose a threat. By picture, I mean screenshot. By threat I mean attacker. What if there was a way to find more exposures without exactly knowing what we’re looking for? OWASP DirBuster had the right idea but was missing the ...
Rob Ragan, Oscar Salazar
Netflix's Layered Approach to Reducing Risk of Credential Compromise
Building a secure system is like constructing a good pizza – each individual layer adds flavor that ultimately builds to the perfect bite. At Netflix we have hand-crafted ingredients that by themself are scrumptious, but when placed together strat...
Travis McPeak, Will Bengtson
Inducing Amnesia in Browsers: the Clear Site Data Header
The Clear Site Data HTTP header is a relatively new mechanism available to web application developers and security teams and offers just what business leaders are looking for: security and privacy benefits with low level of effort. We will share o...
Caleb Queern
Preventing Mobile App and API Abuse
Think a good user authentication solution is enough protection? Think again. Follow the ShipFast courier service’s evolving mobile app and API security approach as it beats back malicious ShipRaider. As ShipFast launches its mobile app with h...
Skip Hovsmith
Keynote - Starting Strength for AppSec: What Mark Rippetoe Can Teach You about Building AppSec Muscles
Fredrick "Flee" Lee, Head of Info Security at Square, powerfully explains how the substance of success is to start small, measure everything, and to specify and practice frequently. Lee goes on to characterize what Mark Rippetoe, bodybuilder and a...
Fredrick Lee
What's Happening in OWASP?
1.OWASP -- Disrupting Web Application Insecurity, Internationally 2.OWASP -- A Global AppSec Community Changing the World For The Better 3.OWASP -- Securing Applications on a Global Level Richard Greenberg, an OWASP pioneer and President of t...
Richard Greenberg
Startup security: Starting a security program at a startup
There's no blueprint for how to be successful at a small startup. Startups are quirky, ambiguous, and full of challenges and broken processes. Startups also have a high risk tolerance and rarely introduce security from the beginning. This talk wil...
Evan Johnson
Leveraging Users' Engagement to Improve Account Security
In this day and age, where companies disclose security breaches almost daily, protecting users data can become a daunting task. Users tend to use the same credentials across different applications and platforms. A third party data breach can end u...
Amine Kamel
Offensive Threat Models Against the Supply Chain
Threat models are often used by security champions to discover flaws in application environments. Many threat models are built thru defensive lens, foregoing realistic attack patterns that reflect adversarial goals vs. simply using a limited, non-...
Tony UcedaVelez
Cache Me If You Can: Messing with Web Caching
As application security gained in popularity and maturity, attackers and researchers have turned to more creative methods for exploiting web applications. In 2017, security researcher Omer Gil introduced the Web Cache Deception attack. This attack...
Louis Dion-Marcil
Open-source OWASP tools to aid in penetration testing coverage
White hat penetration testers are generally at a disadvantage compared to the malicious attackers they help defend against. They have limited time and resources to secure the entire application, whereas attackers have unlimited time and may only n...
Vincent Hopson
Fail, Learn, Fix: Improving Security The Old-Fashioned Way
Fail, Learn, Fix: Improving Security The Old-Fashioned Way Bryan Payne, Director of Engineering Product & Application Security at Netflix, gives a moving, yet persuasive talk at AppSec Cali 2019. In his eloquent talk, "Fail, Learn, Fix: Improvi...
Bryan Payne
How to Lose a Container in 10 Minutes
Moving to the cloud and deploying containers? In this talk I discuss both the mindset shift and tech challenges, with some common mistakes made in real-life deployments with some real life (albeit redacted) examples. We’ll also look at what happen...
Sarah Young
Docker
Cloud Forensics: Putting The Bits Back Together
Cloud computing security response is no different to servers racked in a regular datacenter, except for a key difference: When a server is breached, and the need exists to perform a forensic evaluation of that server, the responder has no idea whe...
Brandon Sherman
An Attacker's View of Serverless and GraphQL Apps
Serverless Technology (Functions as a Service) is fast becoming the next "big thing" in the world of distributed applications. Organizations are investing a great deal of resources in this technology as a force-multiplier, cost-saver and ops-simpl...
Abhay Bhargav
GraphQL
Serverless
CISO Panel: Baking Security Into the SDLC
How are CISOs coping with the rapid changes in application development methodologies and the constant resulting updates and pressures to publish? Where when and how do you get security in the mix? Come here real-world experiences on how CISOs are ...
Bruce Phillips, Shyama Rose, Richard Greenberg, Coleen Coolidge, Martin Mazor
The Art of Vulnerability Management
“I am just going to ignore these tickets until they go away” “These security tickets are ruining my product roadmap” “This is the most obscure corner case of security, this can never happen in real life” “Yes, I’ll fix this in……...2022” We h...
Alexandra Nassar, Harshil Parikh
Slack App Security: Securing your Workspaces from a Bot Uprising
Slack’s developer platform has some powerful functionality that allows you to customize your org’s workflow. But with great power comes great responsibility. While Slack has a robust security posture, do you suffer from insomnia pondering the secu...
Kelly Ann, Nikki Brandt
How to Start a Cyber War: Lessons from Brussels-EU Cyber Warfare Exercises
Nation-state offensive digital attacks are on the rise. Especially considering the news headlines. But, what is cyber warfare and what’s realistic? Come on a journey into a twisted but realistic game scenario with real-world implications. What dec...
Christina Kubecka
Endpoint Finder: A static analysis tool to find web endpoints
JavaScript files contain an increasing amount of information about server endpoint. Existing tools use regex search patterns to extract this information statically. This kind of approach has several limitations. With static code analysis, we can g...
Olivier Arteau
Working with Developers for Fun and Progress
Forging a strong relationship with developers is essential part of creating an impactful AppSec program. Without it, your team will have little idea what's going on and will have trouble getting bugs fixed and features shipped. Segment has built s...
Leif Dreizler
Threat Model Every Story: Practical Continuous Threat Modeling Work for Your Team
The good old days of waterfall! You had "The One Design To Bind Them All" and once it got all agreed, the developers would happily implement it "per spec". But alas, we are not there anymore. Agile methodologies basically guarantee that the deploy...
Izar Tarandach
Keynote - The Unabridged History of Application Security
Jim offers a positive outlook at what the software industry have been going through with application security and how it has improved. Jim Manico, Founder and Lead Trainer Manicode Security, expressively chronicles the application security narr...
Jim Manico
(in)Secure Development - Why some product teams are great and others … aren’t...
In this presentation, Koen will share his experiences with Product Teams at Riot Games and how those teams do or do not take security into consideration. Every product team is unique; but they all behave in similar security patterns, and care abou...
Koen Hendrix
Authorization in Micro Services World Kubernetes, ISTIO and Open Policy Agent
Micro Services enables developers to break down the monolithic application into smaller and manageable micro services. It is accelerated by Cloud Native platform such as Kubernetes and ISTIO. However the challenge of enforcing finer grained author...
Sitaraman Lakshminarayanan
Keynote - How to Slay a Dragon
AppSec Cali 2019, Keynote Speaker, Adrienne Porter Felt, Engineer & Manager for Google, sees the security of Chrome from both sides--from the product team to the end user. Often, there is no one right solution to a problem. Her line of attack in f...
Adrienne Porter Felt
Building Cloud-Native Security for Apps and APIs with NGINX
NGINX is a very flexible platform that can be enhanced with strong security capabilities -- if you know what components you need and how to cook them. With our set of modules and tricks, everyone can get security visibility and real-time protectio...
Stepan Ilyin
Cyber Insurance: A Primer for Infosec
The market for cyber insurance is expected to reach $14 Billion by 2022. Many companies, large and small, have purchased insurance or are in the process of evaluating it. Technical information security professionals are being asked to participate ...
Nicole Becher
Can Kubernetes Keep a Secret?
We’ve all experienced it: you’re working on a task, adding some code, and then you need to store some sensitive configuration value. It could be an API key, client secret or an encryption key ― something that’s highly sensitive and must be kept se...
Omer Levi Hevroni
Kubernetes
A Seat at the Table
The DevOps Movement has won, and all too often, left security wondering what our role is in the new world. Effective collaboration requires new skills, new approaches, and a new speed. We’ll look at all three, how security can collaborate, how we ...
Adam Shostack
Game On! Adding Privacy to Threat Modeling
The Elevation of Privilege card game has been designed for threat modeling based on STRIDE threats, and has since become a widely-deployed tool for security and development teams. One of its many feats is to bridge the knowledge gap between develo...
Mark Vinkovits, Adam Shostack
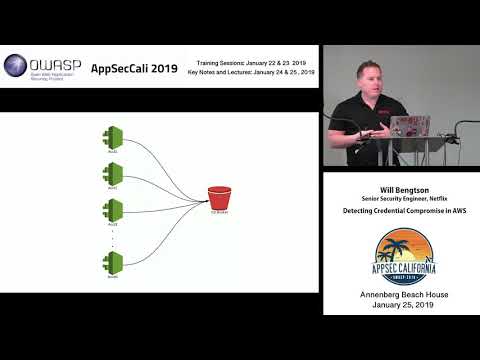
Detecting Credential Compromise in AWS
Credential compromise in the cloud is not a threat that one company faces, rather it is a widespread concern as more and more companies operate in the cloud. Credential compromise can lead to many different outcomes depending on the motive of the ...
Will Bengtson
AWS
It Depends...
From the time we choose to rise each morning, to the time we finally rest our heads, almost every decision made in our daily lives, depends on something. When we understand these dependencies, we are better equipped to control our responses. Manag...
Tania Ward, Kristen Pascale
Securing Third Party Applications at Scale
Third party applications can pose a significant risk to a company. You are forced to trust the maintainer with sensitive data and access to internal networks. As a company scales, managing security across a fleet of third party applications become...
Prashanth Kannan, Ryan Flood
Lessons Learned from the DevSecOps Trenches (Panel)
The adoption of agile development practices and DevOps has enabled companies to iterate more quickly, allowing them to be more responsive to customer needs and deliver features in a fraction of the time. While this rapid release cycle has a number...
Devdatta Akhawee, Astha Singhal, John Heasman, Doug DePerry, Divya Dwarakanath, Clint Gibler
Automated Account Takeover: The Rise of Single Request Attacks
Account takeover is growing. Attackers swoop in after credential spills and use software to automatically match breached email addresses with the top 10 most common passwords. While this approach, known as a single request attack. may appear unsop...
Kevin Gosschalk
A Pragmatic Approach for Internal Security Partnerships
Why do we have such a hard time getting engineering teams to care about vulnerabilities? How is it that we are fixing lots of vulnerabilities, yet are still falling ever further behind on the actual risks? These questions both have the same answer...
Scott Behrens, Esha Kanekar