Global AppSec Tel Aviv 2019
Talks
Breaking out of the container without Zero Day – Can that happen to me?
Organizations are in the process of changing and becoming more agile and to adopt DevOps as way of thinking. Many of them use Docker and Containers in order to implements those concepts in effective, Accurate and secure way. The changes from the t...
Asher Genachowski, Chen Cohen
Docker
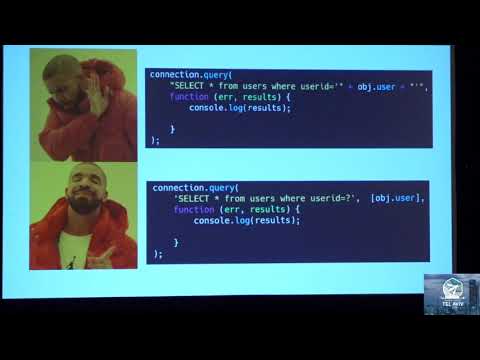
Securing Node.js and JavaScript
In this talk, we will see what security issues can be found in the Node.js and JavaScript world and how to successfully protect against attackers. Vladimir de Turckheim Software Engineer, Sqreen V. works as a software engineer at Sqreen where...
Vladimir de Turckheim
JavaScript
Node.js
Insights from the trenches must have secure coding lessons in mobile
In this session we’ll present common coding pitfalls of mobile app developers, present their real-world ramifications and provide guidance on how to avoid them. The presentation will include demonstrations of techniques that attackers use to overc...
Yair Amit, Igal Kreichman
Vehicle Security Trends Implications for Automotive Suppliers
As the automotive industry continues to introduce bleeding edge technology, vehicles have become increasingly intelligent expanding the automotive attack surface far beyond traditional paradigms. We are living in a world of connected and autonomou...
Aaron Guzman
Three levels of complexity: Threat Modeling of Containerized Application
Threat Modeling is a very powerful tool of Application Security; however, many organizations are struggling to use it. There is a common perception that the Threat Modelling is too heavy and should be done only at specific stages of development pr...
Elena Kravchenko
Can We Automate Security?
This talk will focus on the tools that Microsoft built into our CI/CD pipelines to secure the products and services we are deploying, and the lessons we've learned along the way. Sasha Rosenbaum Azure DevOps Program Manager, Microsoft Sasha i...
Sasha Rosenbaum
Defending Cloud Infrastructures with Cloud Security Suite
Nowadays, cloud infrastructure is pretty much the de-facto service used by large/small companies. Most of the major organizations have entirely moved to cloud. With more and more companies moving to cloud, the security of cloud becomes a major con...
Ayesh Chauhan
Building & Hacking Modern iOS Apps
After my offensive presentation "Testing iOS Apps without Jailbreak in 2018" it is time to focus also on building not just breaking. This talk will cover the most important milestones in reaching secure iOS/macOS apps. I'm going to show you how to...
Wojciech Regula
iOS
Testing and Hacking APIs
Most of the modern applications that have been developed in the last years deeply rely on APIs, including web, mobile and IOT apps. APIs are different than traditional web servers in many ways. This change might be confusing and challenging for p...
Inon Shkedy
OWASP Global AppSec Tel Aviv 2019 - Innovation Fair
This year in Global AppSec Tel Aviv we will run, for the first time, an innovation fair for startups in the area of Application and Software Security. This fair is an opportunity for early-stage startups (younger than 3 years, with less than 1M$ r...
Unknown
The Evolving Community of Appsec
Application Security as a discipline has continuously evolved over the last couple of decades. This is an expected outcome of the growth and maturity of this engineering discipline. At the same time, technology has continued to become more pervasi...
Astha Singhal
DevSecOps with OWASP DevSlop
The OWASP DevSlop team is dedicated to learning and teaching DevSecOps via examples, and “Patty the Pipeline” is no exception: we ensure all the 3rd party components are known-secure, retrieve secrets from a secret store, and the code must pass ne...
Tanya Janca, Nancy Garche
Crypto Failures - And not just in bitcoin
Crypto used to mean cryptography - and the business of older mathematicians with a serious demeanor. Nowadays, everyone wants some crypto, be it coins, ICOs or similar offering. What people forget though is that crypto is hard - and putting real m...
Guy Barnhart-magen
Crypto
Are we making our engineers blue?
Our engineers are going from software engineers to software + infrastructure + network + database engineers, and they’re delivering faster. In an environment of continuous deployment how can we ensure that as security teams we’re scaling as fast a...
Tash Norris
Security for Modern Webapps: New Web Platform Security Features to Protect your Application
Web applications have historically been plagued by vulnerabilities which allow attackers to compromise the session of a logged-in user: XSS, CSRF, clickjacking and related issues. Luckily, new security mechanisms available in web browsers in 2019 ...
Lukas Weichselbaum
OWASP Serverless Top 10
In moving to serverless, we shift some security responsibilities to the infrastructure provider by eliminating the need to manage servers. Unfortunately, that doesn’t mean we’re entirely absolved of all security duties. Serverless functions still ...
Tal Melamed
Serverless
How Online Dating Made Me Better At Threat Modeling
Isaiah has used online dating sites such as Tinder and OkCupid. At times this seems antithetical to his stance on privacy and security. To better understand the security ramifications of online dating, and to establish safer methods of doing it, h...
Isaiah Sarju
NOSQL web application vulnerabilities and mitigation
NOSQL data storage systems have become very popular, due to their scalability and ease of use. I will examine injection methods, CSRF vulnerabilities, and mitigation solutions. Moreover, NOSQL does authentication, encryption, and role management...
Amir Luckach
NoSQL
Bringing Rapid Prototyping To The Threat Model Process
Threat Modelling is a powerful way of discovering security risks during software architecture and design. It can be used to build security into software and remove design flaws before actual code development starts. However, it can be a laborious ...
Geoffrey Hill
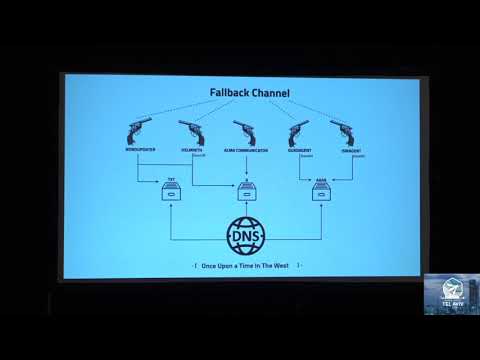
Once Upon a Time in the West - A story on DNS Attacks
Just like in Old West movies, we are going through a land riddle with well-known gunmen: OceanLotus, DNSpionage and OilRig among others, who roam at ease, while the security cowboys sleep. This presentation will uncover the toolset and techniques ...
Ruth Esmeralda Barbacil, Valentina Palacin
The Importance of the Cloud and the Developers Communities in Fighting Cyber Crime
Michal Braverman-Blumenstyk CTO, Cloud and AI Security Division, Microsoft Michal Braverman-Blumenstyk is the CTO of Cloud and AI Security division, Microsoft. Michal and teamare driving the Microsoft security strategy and innovation. Prior to h...
Michal Braverman-Blumenstyk
Injecting Security Controls in Software Applications
Cyber attacks are a real and growing threat to businesses and an increasing number of attacks take place at application layer. The best defense is to develop applications where security is incorporated as part of the software development life cycl...
Katy Anton
Trusted Types: End to end injection safety at scale
18 years have passed since Cross-Site Scripting (XSS) became the single most common security problem in web applications. Since then, numerous efforts have been proposed to detect, fix or mitigate it, but these piecemeal efforts have not combined ...
Mike Samuel, Krzysztof Kotowicz
Testing Security In, the Right Way
Developing secure software requires a solid SDLC, including all team members throughout ALL stages of the process, from requirements through implementation. So how come we always ignore QA? Why do we often talk about developers as security cham...
Iris Levari, Adi Belnikov
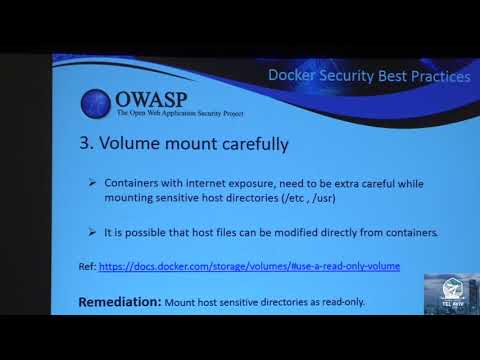
Docker Security Insights
As innovation in technology increases, security becomes trickier. In order to embrace latest technologies like Docker and Kubernetics, Product IT organizations must consider security as top priority. Containers vulnerabilities like “Dirty Cow”, “E...
Sujatha Yakasiri
Docker
Black Clouds and Silver Linings in Node.js Security
With a great ecosystem, comes great responsibility, and application security is not one to wave off. Let’s review some black clouds of security horror stories in the Node.js ecosystem, and learn how to mitigate them to build secure JavaScript and ...
Liran Tal
JavaScript
Node.js
OWASP Top 10 for JavaScript Developers
With the release of the OWASP TOP 10 2017 we saw new issues rise as contenders of most common issues in the web landscape. Much of the OWASP documentation displays issues, and remediation advice/code relating to Java, C++, and C#; however not much...
Lewis Ardern
JavaScript
What do you mean threat model EVERY story
We are all going continuous these days. Continuous delivery, integration - but what about Threat Modeling? How do we bring this (traditionally) heavy activity into the new "speed" of development, integrate and educate developers and reflect the co...
Izar Tarandach
Protecting a High Profile Enterprise
In this talk, I will share my 20+ years’ experience in protecting large and small, multinational and high profile enterprises. I will present strategies and disciplines, and how do the CISO and the executive teams choose the right one for the org...
Yoram Golandsky
Looking Towards the Future of Open Source Vulnerability Management
Open source usage has become a mainstream practice — it’s impossible to keep up with today’s pace of software production without it. The rise in open source usage has led to a dramatic rise in open source vulnerabilities, demanding that developmen...
Shiri Ivstan
Dissecting Mobile Application Privacy and Analytics
Have you ever wondered how much data your favorite business application is capturing during your mobile app visits? Are you a developer or security engineer tasked with keeping your client data secure? Are you curious about what kind of data that ...
Kevin Cody
Software Security War: your reports are dead!
The talk will introduce the new OWASP Software Security 5D Framework showing the assessment data of various International companies. The evolution of software security verification activities: from firm reports on desks to the integration of se...
Matteo Meucci
Uninvited Guests Understanding Malicious Web Bots with OWASP Handbook
Scalping, Scraping, Skewing, Sniping … oh my! What are they? How do you wrap your mind around malicious bots and unwanted automation? Presented by a co-leader of the OWASP project on automated threats, this talk will help you navigate the swamplan...
Tin Zaw
Who left open the cookie jar?
Nowadays, cookies are the most prominent mechanism to identify and authenticate users on the Internet. Although facilitating important usability advances, they also opened the door to cross-site attacks and third-party tracking. Various countermea...
Tom Van Goethem
Rhyming with Hacks - the Ballad of Supply Chain Attacks
2018 was big on Supply Chain Attacks (SCA), with big e-commerce companies such as British Airways or Ticketmaster being targeted. The cyber criminal groups behind some of these attacks are referred to as Magecart. During this talk, we'll presen...
Pedro Fortuna
Security Culture Here be Hackers
RFC1983 clarifies hacker term as "a person who delights in having an intimate understanding of the internal workings of a system, computers and computer networks in particular". Let's say we want our developers and other IT stuff be security hacke...
Taras Ivaschenko
Struts 2 Must Die The Life and Inevitable Death of Java’s Spaghettiest™ Framework
Struts2 Java framework has started as a cool modern framework and ended up like a bomb periodically exploding into security teams’ faces. Now it’s impossible to get rid of from production and it may lead to massive damage like Equifax breach becau...
Eugene Rojavski
Java
Webhooks Hookups Abusing API Developers
The concept of a Webhook is quite simple: an HTTP callback that occurs when something happens. However, Webhook's powerful nature of open ended integration with arbitrary web services, makes it very easy for API developers to pipe data in and out ...
Tomer Zait, Maxim Zavodchik
How NLP Can Help Us Understand Web Attackers
Word2Vec is a popular Natural Language Processing approach, which was imported by different domains (as Something2Vec), embedding domain objects in Euclidean spaces for similarity/distance calculation, clustering, visualization and more. We will ...
Ori Or-Meir, Itsik Mantin
Magecart - A Growing Threat to E-Commerce Sites
In the last two years, we’ve observed a growing threat for e-commerce sites: Magecart. By using a cocktail of 0-days and known de-serialization bugs in the Magento platform and Magento extensions it managed to impact major web sites such as Britis...
Simon Kenin, Ziv Mador
Common API Security Pitfalls
The shift towards an API landscape indicates a significant evolution in the way we build applications. The rise of JavaScript and mobile applications have sparked an explosion of easily-accessible REST APIs. But how do you protect access to your A...
Philippe De Ryck
“Alexa and Cortana in Windowsland”: Hacking an Innovative Partnership and Other Adventures
This is a presentation about the essence of Cyber Security – what happens when you take new and innovative concepts, spice them up with business partnerships and plug them into existing security mechanisms. In our talk, we will demonstrate a va...
Amichai Shulman, Yuval Ron
Automated Cyber Security Platform at Scale
Automated Security and Security Orchestration is the new way of tackling very sophisticated threats and cyber crime. The volume of data, processes, procedures and workflows are overwhelming, making human power and expertise insufficient to work wi...
Ovidiu Cical